Software Composition Analysis
SCA, but with reachability analysis that cuts 92% of noise.
Your developers use open source packages, AI models, and AI services. Find out what they're using and fix risks fast.

How it works

1
Identify all dependencies
Go beyond classic SCA to discover all direct and transitive dependencies, including AI models and services.

2
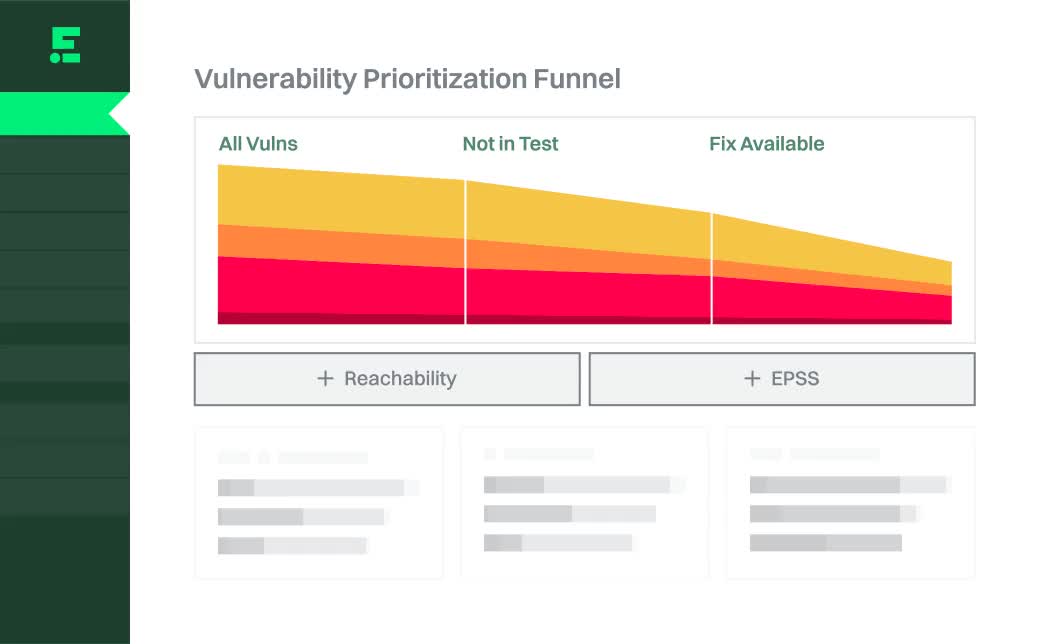
Prioritize by danger
Combine reachability and EPSS to determine which vulnerabilities are the most dangerous, and remediate those first.

3
Fix faster
Identify upgrades that can be performed without risk of breaking changes and help engineering plan for the hard ones.
Securing code written by humans and AI at:


































































Without the tedium and minutia of tracking down individual items that might not matter, we can focus on the remaining vulnerabilities that would impact customers and our FedRAMP compliance."





