Policies and operational workflows aren't exactly the hottest conversation starters at parties (trust me on this). But when designed thoughtfully, they can drastically simplify life for developers and security teams alike.
Traditionally, security policies feel like blunt instruments, "Break the build whenever a critical vulnerability pops up!", leading to endless Jira tickets. But one-size-fits-all approaches rarely work because every organization's environment and risk tolerance are unique.
Why most security policies frustrate developers
Developers don’t get into engineering because they love fixing security tickets. They want to build software. They love creating things, seeing their code compile, running features they’ve spent hours on, and solving complex technical challenges. And they do want their code to be secure.
What they don’t love:
- A flood of security tickets that don’t seem relevant
- Breaking builds over vulnerabilities that aren’t even reachable
- Spending hours upgrading dependencies that pose no real risk
Many security tools claim to be developer-friendly, but that usually translates to “we integrate into the IDE” or “we shift security detection left.” In reality, developer-friendly means providing the right context at the right time so engineers can focus on building securely.

How Endor Labs’ policies reduce friction
Instead of overwhelming developers with noise, policies should ensure that security interventions:
- Surface only meaningful findings (things that actually matter)
- Provide clear guidance on fixes (so developers don’t have to guess)
- Automate remediation where possible (reducing manual effort)
Endor Labs flips the script. Instead of generic, chainsaw-style policies, we give you precise, scalpel-like controls tailored to your actual environment and risks. This precision ensures security teams focus only on the truly impactful issues, making developers' lives easier and keeping security interventions meaningful.
How finding and action policies streamline security at Endor Labs
At Endor Labs, we use finding and action policies to help deliver this precision. Let’s take a closer look at how each type works.
1. Finding Policies
These do exactly as promised—identify issues beyond just vulnerabilities. We're talking end-of-life dependencies, risky maintainers, outdated libraries, or even eyebrow-raising configurations. With over 150 data points per dependency—including maintainership status, repository activity, commit frequency, and community health—finding policies empower your team to proactively manage risks.
Real-world example: A financial institution customer needed to pinpoint Django 4.2 usage, which was approaching end-of-life. Endor Labs not only identified every instance of Django 4.2 across their projects but also provided developers with clear, actionable upgrade paths. This saved significant time by eliminating manual audits and reduced potential risks associated with outdated dependencies.
Another example: A large enterprise discovered it had legacy dependencies with no available patches for critical vulnerabilities. Using customized finding policies, Endor Labs accurately flagged these dependencies, enabling teams to quickly devise strategic responses, including migration plans and implementing compensating controls.
2. Action Policies
These automatically trigger specific actions based on findings—such as breaking builds, creating Jira tickets, or notifying teams via Slack—but only when genuinely necessary. Action policies are highly configurable, ensuring builds break rarely, and only for critical, verifiable threats.
For instance, an Endor Labs action policy can be set to only break builds when a vulnerability meets specific criteria:
- High or critical severity
- Verified reachable vulnerability within the dependency
- Available patch or upgrade that safely addresses the vulnerability
- Applies only to production or internet-facing applications
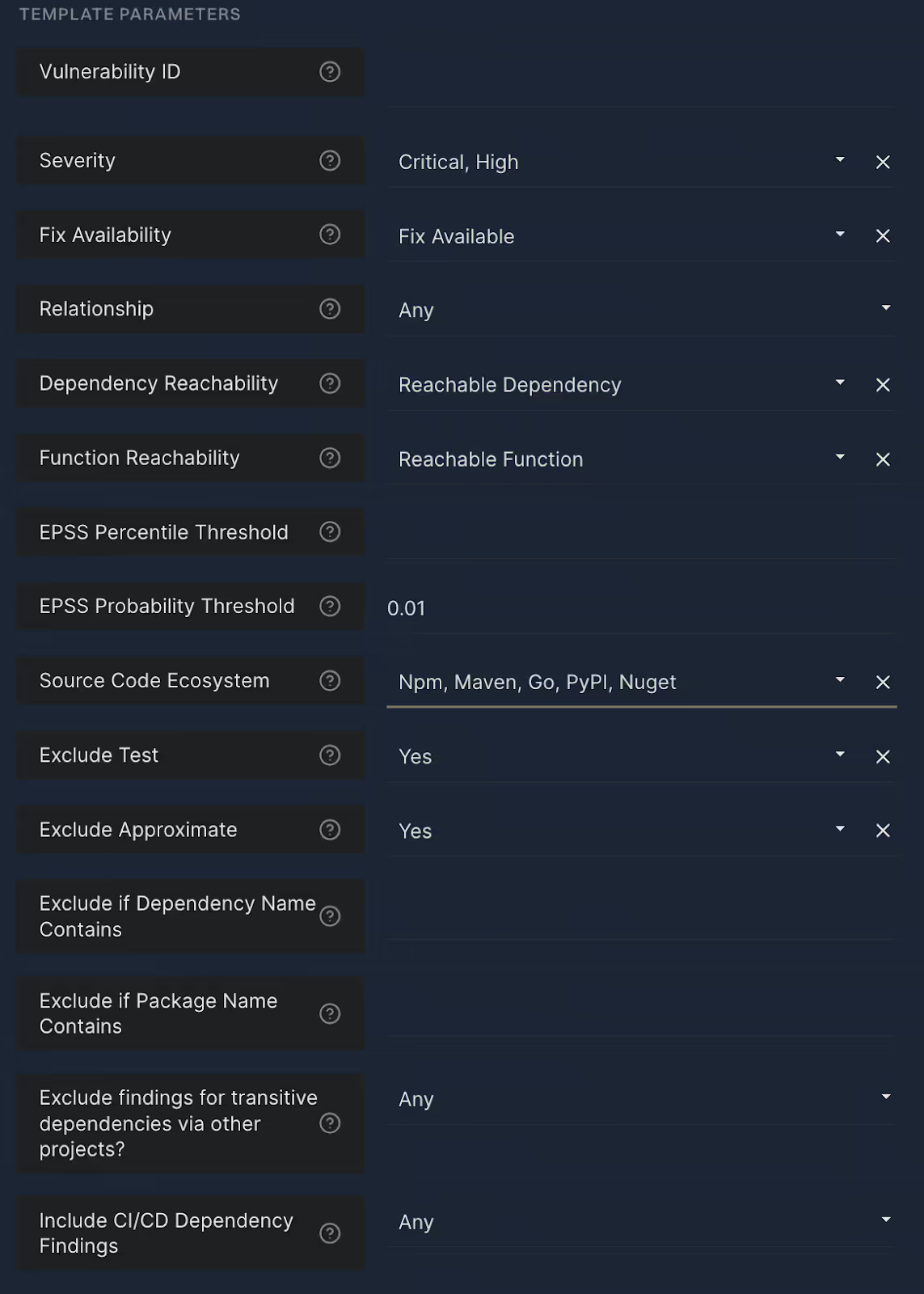
Real-world example: Previously, developers at one fintech company faced frequent build interruptions for vulnerabilities that weren't exploitable or fixable. After implementing Endor Labs' precise action policies, they reduced monthly security Jira tickets from 2,600 to just 140. This transformation significantly boosted developer productivity and morale, as security interventions became rare and trusted, rather than a constant source of frustration.
The real meaning of "developer-friendly"
At Endor Labs, developer-friendly means drastically fewer and more meaningful security interruptions. When a developer's build breaks due to security, it must be for a reason they trust and respect.
Our policy engine ensures exactly this. By narrowing down alerts to what's genuinely actionable, developers stay engaged, productive, and happier. And security? They become an ally, not an adversary.
Stay tuned for our next blog, where we'll dive deeper into Exception and Remediation Policies—explaining how Endor Labs ensures upgrades won't accidentally break your apps and why custom policies are a game-changer for precise, risk-aware automation.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:










