Upgrades and Remediation
Fix CVEs 6.2x faster, without breaking changes
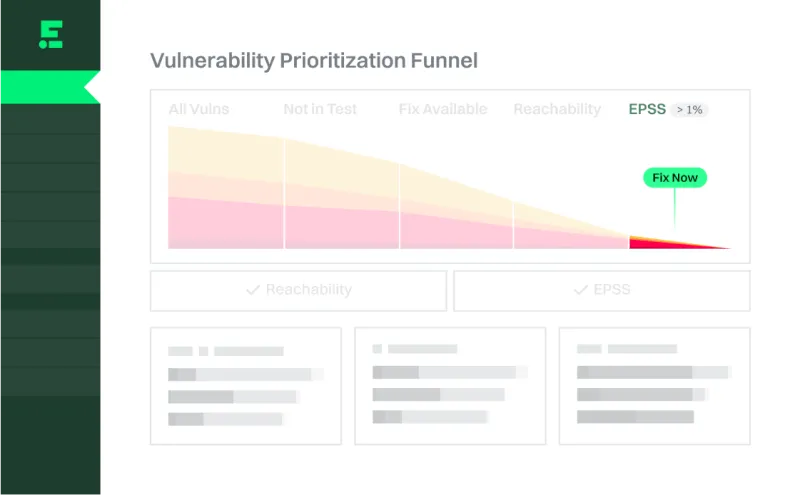
What might seem like a simple version change can have a cascading effect of breaking changes. We help you fix what’s easy and patch what’s hard.
Trusted by Leading Teams


































































How it works

1
Find the riskiest packages
Confirm a vulnerability is reachable and likely to be exploited.

2
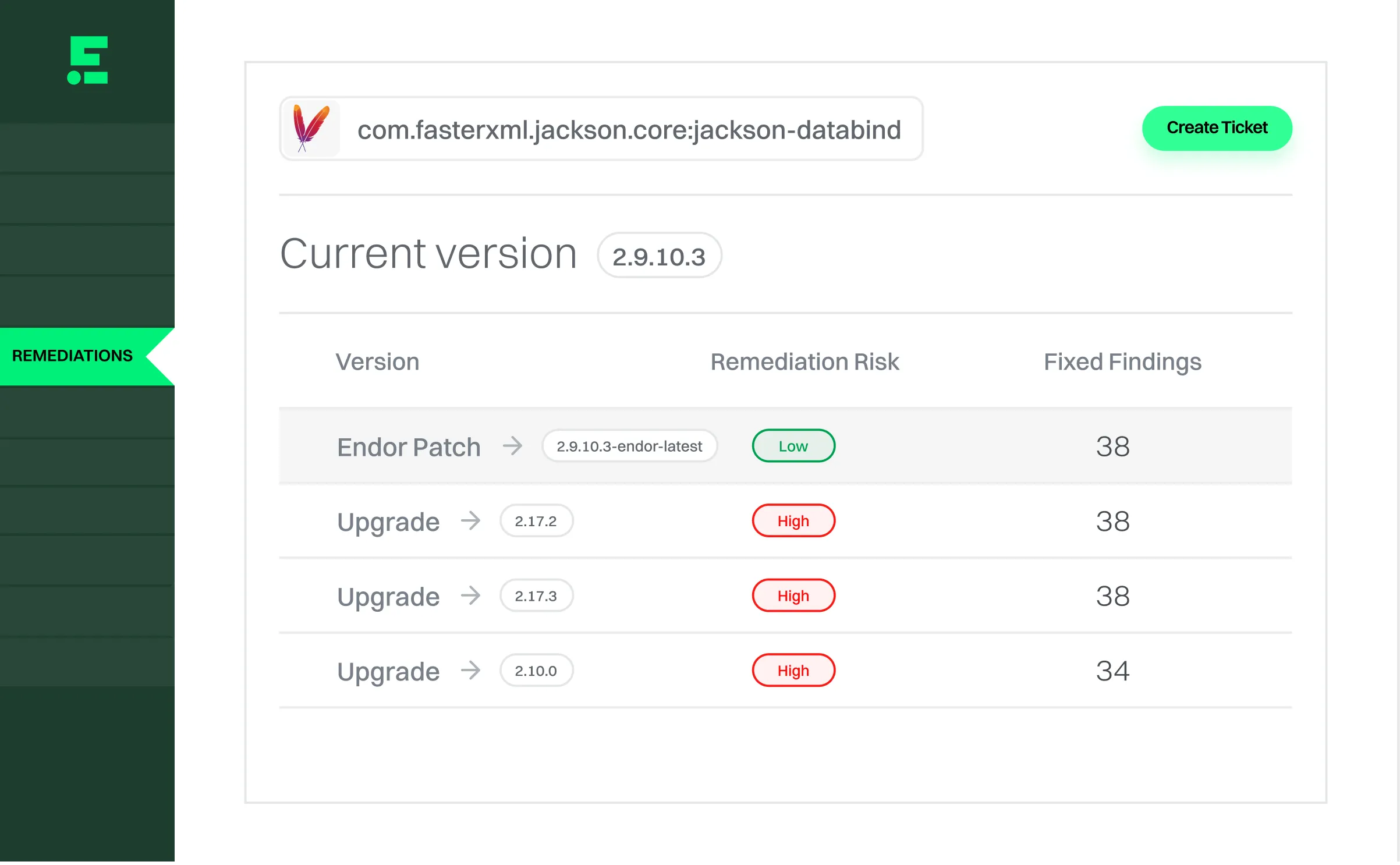
See the effort to remediate
Quickly understand the effort and impact of upgrading to a non-vulnerable version