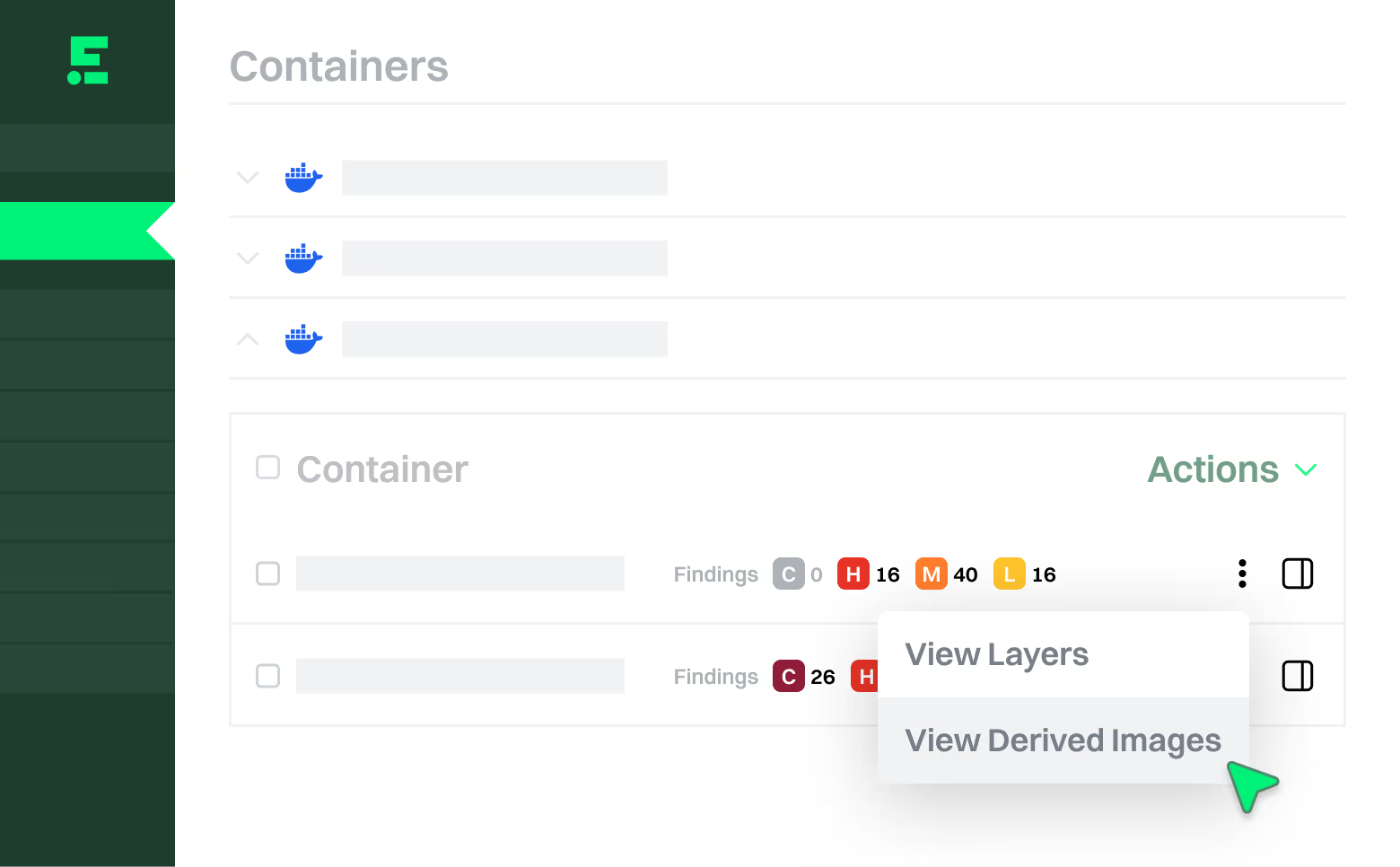
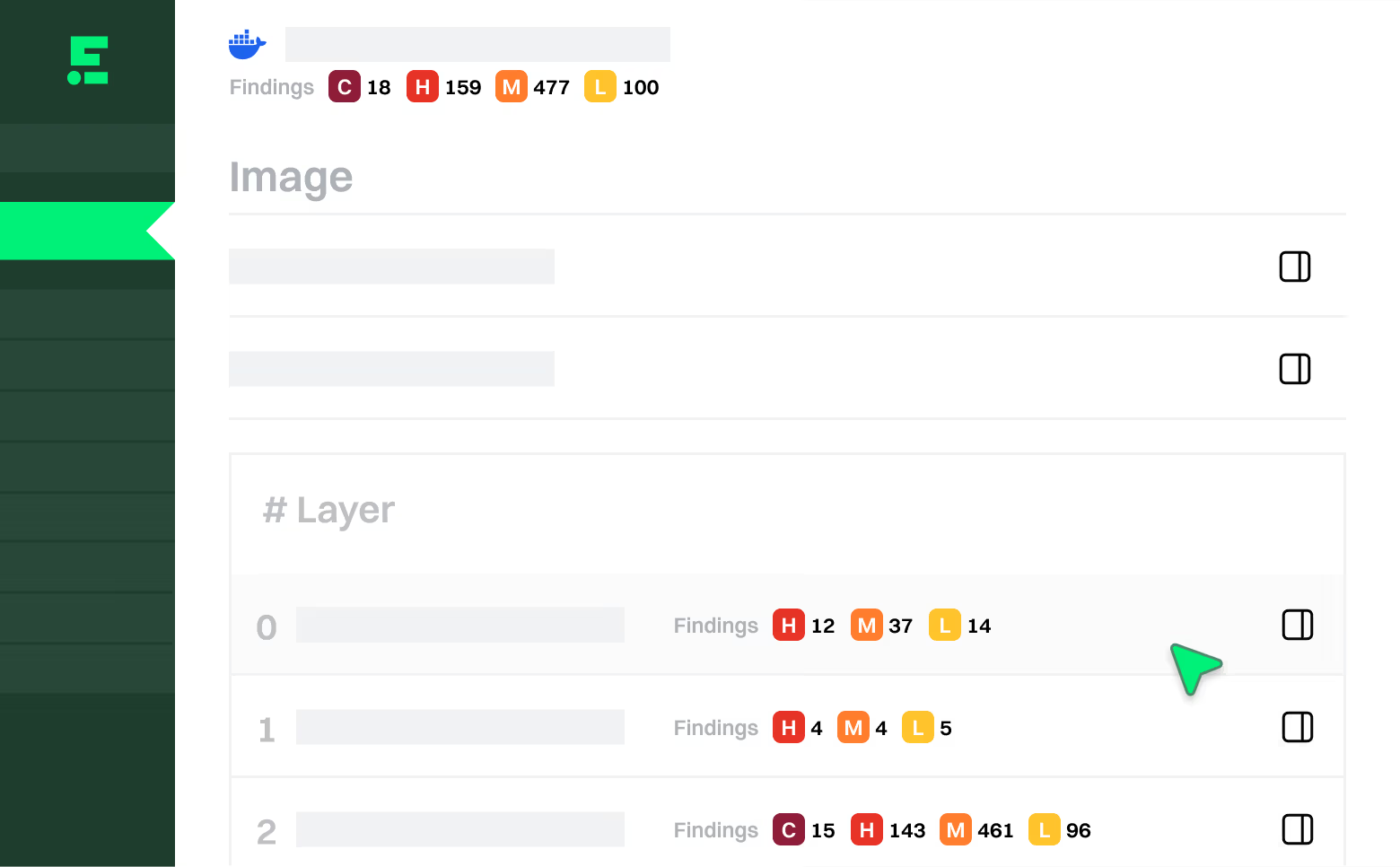
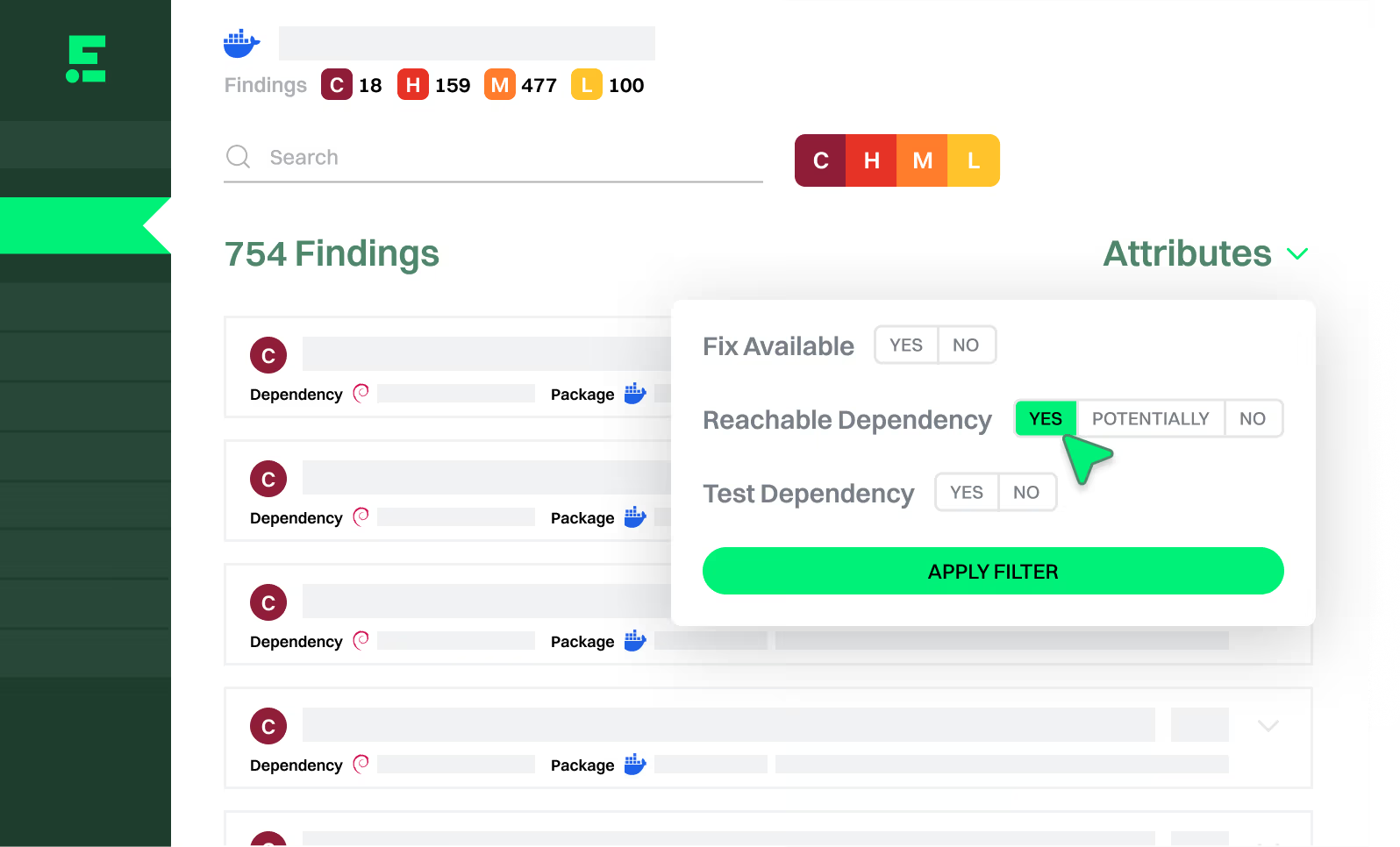
Container Scanning
Cut container image vulnerability noise up to 90%
Endor Labs uses full-stack reachability analysis to help you patch what runs and prune the rest.

How it works

1
Full-stack reachability
Combine static and dynamic analysis of container images to identify which OS packages are reachable in your base images.

2
Lower FedRAMP costs
Avoid double filings with automatic deduplication across SCA and container image findings. One ticket, one fix.

3
Single pane of glass
See all your SAST, SCA, and container findings in one place with central management and visibility.
Securing code written by humans and AI at:


































































Our FedRAMP environment requires more rigor than you would normally get in any other kind of product release, with near zero tolerance for vulnerabilities. Endor Labs’ reachability analysis and consolidated findings reduced the number of true positives requiring remediation, which is a huge time- and money-saver.”