AI Security Code Review
See how each pull request impacts security
Analyze every pull request across your organization for changes to your application’s security architecture — and detect risks that traditional scanners never see.
How it works
1
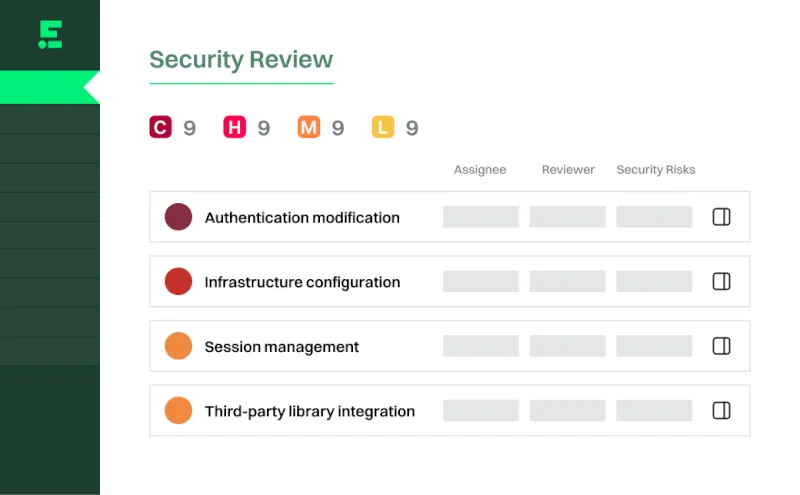
Surface what matters
Scan every pull request to understand what changed and how it impacts security.
2
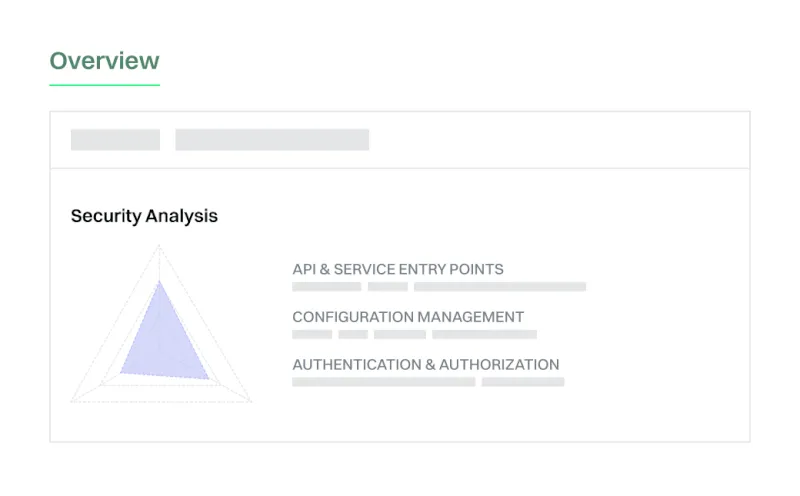
Get context about changes
Summarize and ask questions about changes so you can get up to speed quickly.
3
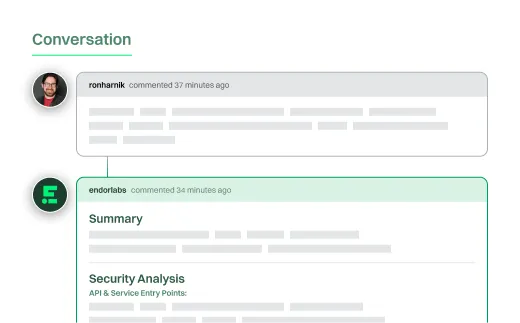
Take action on findings
Route changes to the right stakeholders, enabling fast review and rapid resolution.
Securing human and AI-generated code at:


































































“We’re looking for better ways to scale how we identify business logic risks and unknown unknowns in our codebase. Traditional static analysis tools haven’t really given us the lift we need. Being able to detect risks that we’d otherwise miss manually or through traditional automation would be hugely valuable.”