Shipping containers with end-of-life (EOL) operating systems or packages introduces silent and persistent risk. These components receive no security patches and often no upstream visibility into newly discovered issues. Yet they continue to appear in production images.
To help AppSec teams identify and eliminate this risk early, Endor Labs now supports automated detection of EOL components in container images.
Real-World Example: EOL packages in Ubuntu image
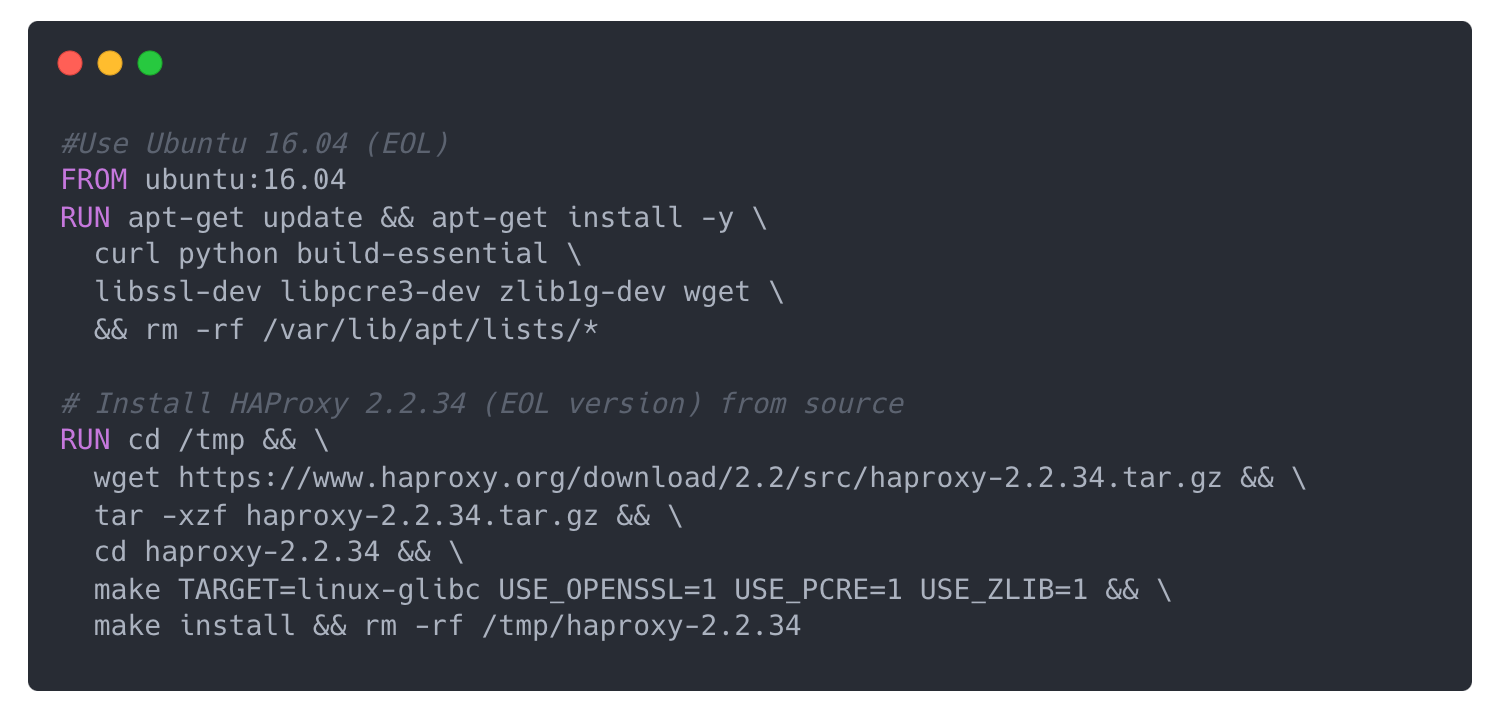
We built a container using ubuntu:16.04 and installed HAProxy 2.2.34 from source. Both are no longer supported by their respective maintainers.
Dockerfile excerpt:
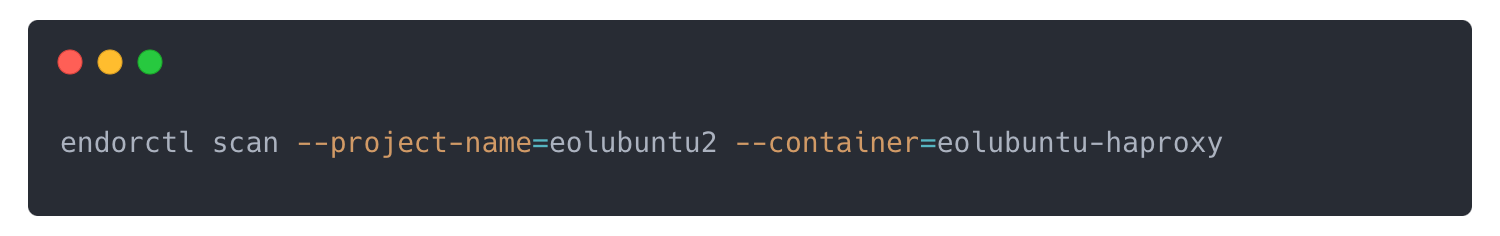
We then build the image and run a scan with the Endor Labs CLI:
What Endor Labs Detects
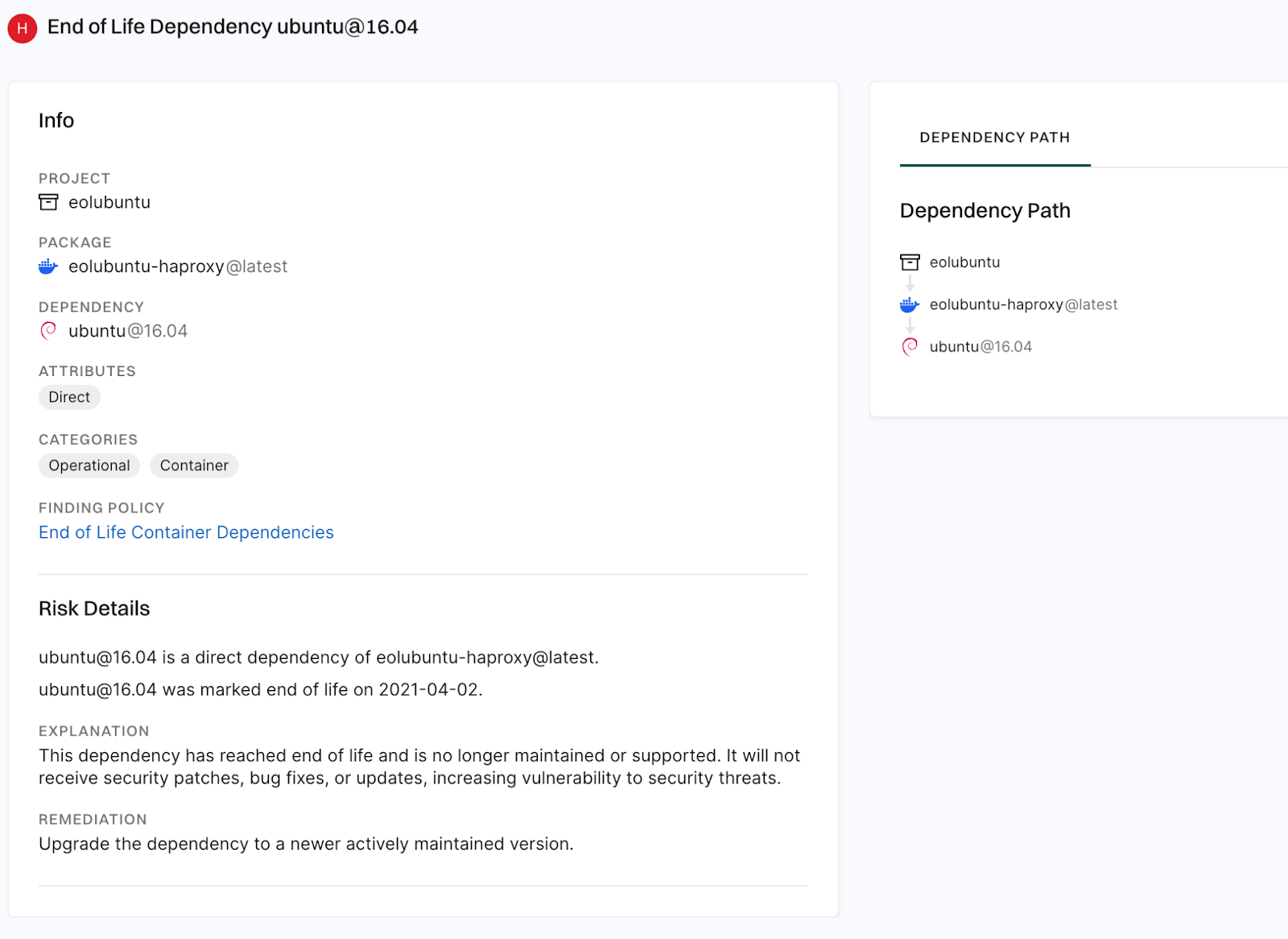
Endor Labs flags the EOL operating system (e.g., ubuntu:16.04):
And the package with the published end-of-support date (e.g., haproxy@2.2.34):
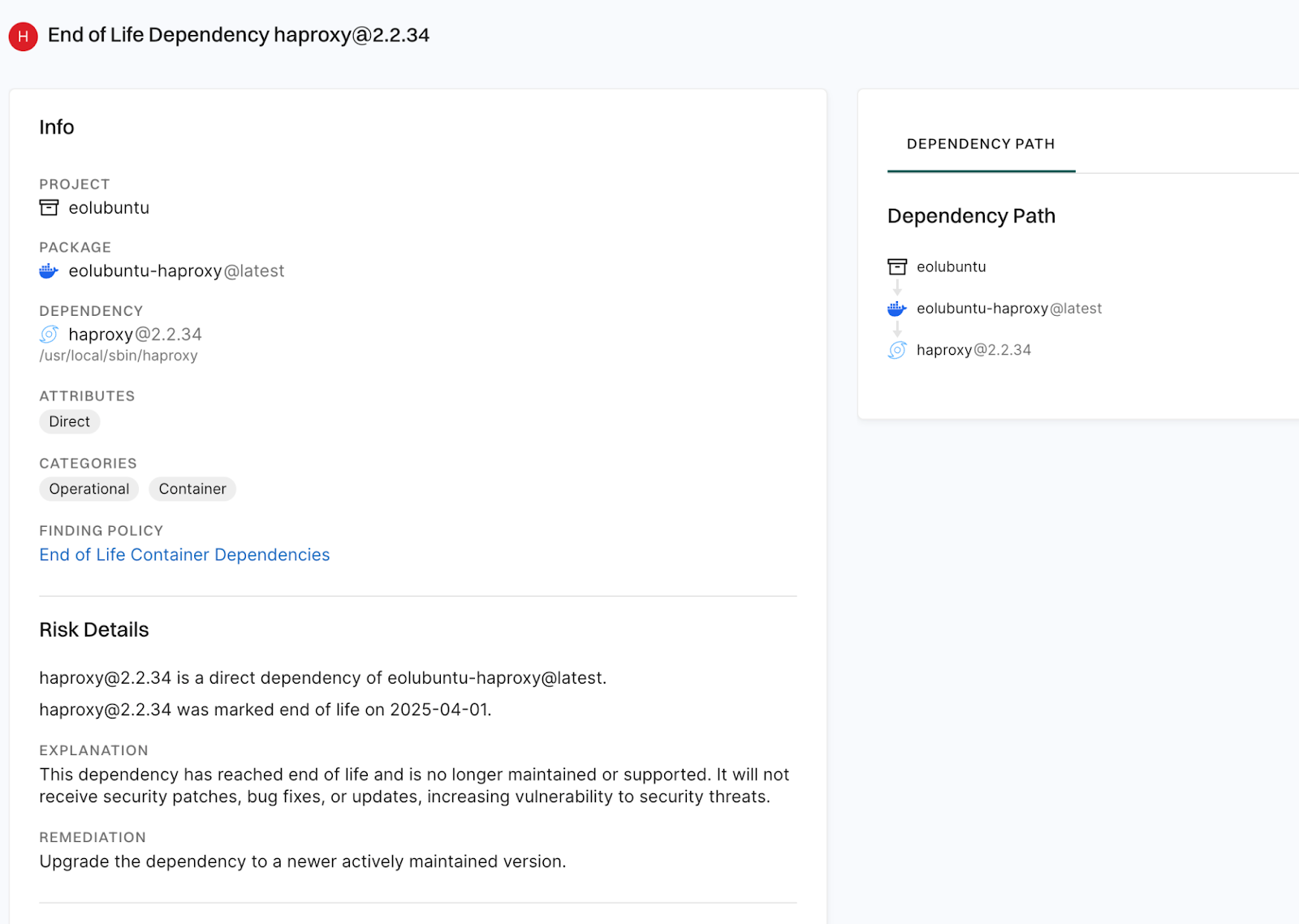
Each finding includes metadata like the dependency name and end-of-support date. All results appear as structured findings, exportable via API or surfaced in the UI. This kind of visibility allows teams to catch unsupported software early in development or CI pipelines, rather than discovering it in runtime environments.
Data Sources and Distro Coverage
Our EOL detection is powered by lifecycle metadata from public, actively maintained sources, and we support major distros such as:
- Ubuntu (e.g., 22.04 LTS supported until 2032, 16.04 EOL in 2021)
- Debian (e.g., Debian 9 "Stretch" EOL in 2022)
- Alpine Linux (e.g., Alpine 3.10 EOL in 2021)
- Red Hat Enterprise Linux (e.g., RHEL 8 supported until 2030)
- And others distros i.e. Fedora, Amazon Linux and Oracle Linux
Coverage is based on official upstream support timelines, including extended maintenance dates when available.
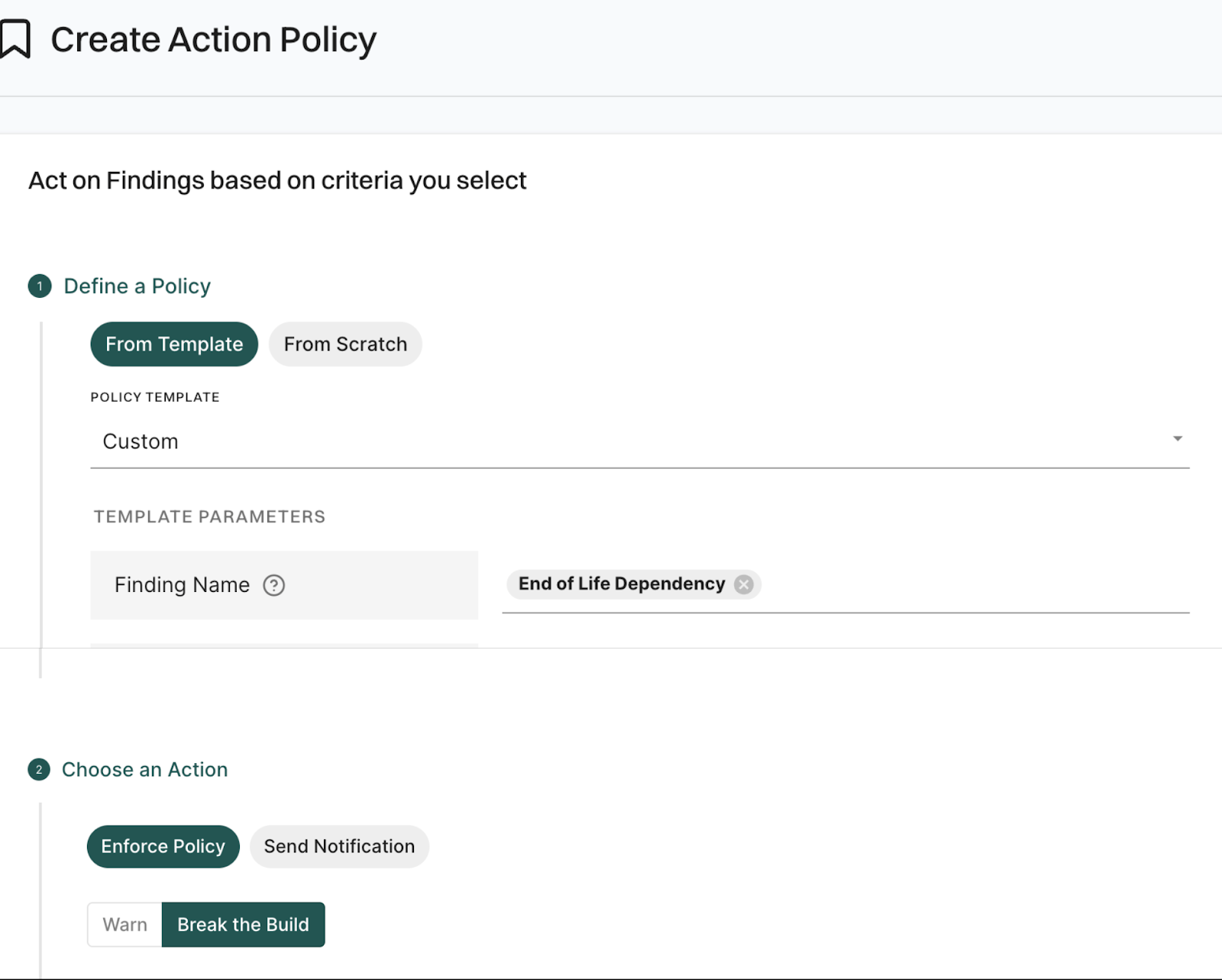
Building policy-based workflows
Endor Labs includes a flexible policy engine that application security and platform engineering teams can use to implement guardrails governing EOL software components in containers.
For example, that might involve failing builds if unsupported components are detected during CI scans. Below example shows how to create an action policy that can warn/block builds if a container EOL finding has been raised.
Final Thoughts
End-of-life software in containers represents a significant security risk. EOL detection is now a core part of container scanning in Endor Labs, and part of our larger solution to help security and engineering teams secure the software supply chain. Built on trusted lifecycle data from public sources, it gives AppSec teams the visibility they need to eliminate unsupported software before it ships.
Learn more about Endor’s container scanning capabiltiies and book a demo today!
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:







