We’re excited to announce the expansion of the Endor Labs Software Supply Chain Security (SSCS) platform to cover CI/CD security! With the addition of Endor Labs CI/CD you can now protect and prioritize impactful risks across the two major components of SSCS: Open source code and CI/CD pipelines.
What is CI/CD Security?
CI/CD (encompassing Continuous Integration, Continuous Delivery, and Continuous Deployment) represents a streamlined, automated pipeline designed to deliver new versions of software. This pipeline is instrumental in integrating automation and continuous monitoring into the app development lifecycle. The primary objective is to reduce human error, accelerate the development process, and ensure the consistent delivery of high-quality code.
However, it's crucial to recognize that CI/CD pipelines often have few security controls out-of the box. This gap can lead to the introduction of vulnerabilities and malware in software by malicious actors, which in turn can compromise the integrity, confidentiality, and availability of the application and its data.
CI/CD Security, also called Software Pipeline Security, is the series of security and compliance safeguards integrated into the building, testing, and deployment steps of your software factory. If code scanning tools help you secure the code itself, CI/CD Security helps you secure the pipelines that build and deploy that code. Ideally, these security measures don’t come at the expense of development speed or agility.
CI/CD Security and Software Supply Chain Security (SSCS)
SLSA defines the software supply chain as “the sequence of steps resulting in the creation of an artifact.”
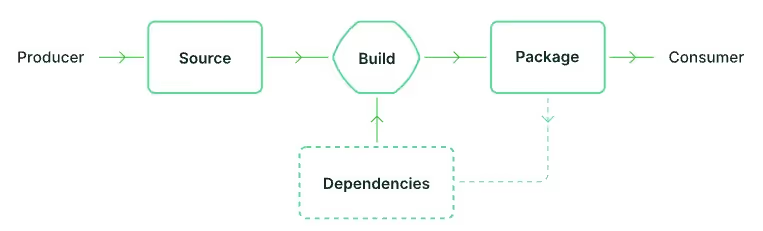
SSCS provides the guardrails and controls that secure the software development lifecycle, all the way to deployment. CI/CD security covers the visibility, integrity and security posture of the pipeline itself, while controls such as Software Composition Analysis (SCA), Secrets Detection, Infrastructure-as-Code (IaC) scans and Static Application Security Testing (SAST) cover the security of code that is shipped through those pipelines. These are two sides of the same coin: High profile supply chain attacks such as the SolarWinds compromise (Sunburst), CodeCov breach, and the recent Okta breach are challenging for security scanners to prevent, but could potentially be defended against through pipeline hardening. In these cases, components along the pipeline were compromised, while security teams either had no visibility or no effective detection and response mechanisms.
Endor Labs sees SSCS as a combination of:
- Code security (with a focus on open source dependencies as they make up 90% of most applications),
- CI/CD security (as detailed in this article), and
- Compliance management across the pipeline
CI/CD Security Challenges
When designing a CI/CD security program, your attention spans the entire software development lifecycle. When focusing on the hardening, security, and discoverability of software pipelines, there are main areas to consider:
Challenge #1: Shadow Engineering & Rogue Repositories
Developers are incentivized to leverage automated tools that help them ship faster. These can be third-party extensions, CI/CD tools, or other apps found on Source Code Management (SCM) marketplaces, such as the GitHub marketplace. Like in the early days of cloud, this has tremendous value in terms of agility but also introduces the challenge of shadow engineering. This is when developers use code repositories, tools or processes that are unsanctioned, untracked, or don't adhere to organization's best practices. This lack of visibility and control can result in unknown vulnerabilities and malware, compromise code integrity, and create compliance issues.
Challenge #2: Security Coverage
Security tools, such as SAST, SCA, IaC, and Secret scanners, are a necessity to protect the SSCS. In addition to selecting the best tools for the job, the way they’re integrated into pipelines is also critical. Even the best of tools can be disruptive to development workflows when they aren’t implemented and managed effectively. And depending on organization size, there may even be some uncertainty about which tools are in which pipelines. The first step towards an effective management strategy is visibility: The ability to see what tools are deployed across each code repository and CI/CD pipeline.
Challenge #3: Compliance
Various stages of the SDLC may need to adhere to different compliance standards, which need to be measured and reported on by various teams. Do the applications being built have an accurate SBOM? Can you demonstrate this with a standard-format SBOM document? Do you have accurate information about vulnerabilities in the components reflected in the SBOM? Can you demonstrate this with a VEX document? Does the security coverage across the pipeline satisfy compliance requirements for SOC2, PCI, and other standards? Do our pipelines help us achieve the desired SLSA level or match up with the NIST SSDF best practices? These questions can become challenging to answer in sprawling environments.
Endor Labs CI/CD
Three core beliefs drove us to build Endor Labs:
- Developers should have the right to choose the best tools for the job, with the appropriate organizational guardrails to manage risk.
- Security can’t afford to be a “tax” on development but instead security teams must help make developers more productive.
- Code and pipeline security go hand in hand: Security scanners don’t mean anything if the pipeline is compromised, and the other way around.
At launch, Endor Labs focused on open source software (OSS) security, which encompasses selecting better dependencies, prioritizing function-reachable vulnerabilities, and reducing technical debt by detecting operational risks (such as unmaintained dependencies). With this major release, security and engineering teams can secure the two core components of the software supply chain: code and the pipelines that ship it. Endor Labs CI/CD Security focuses on three core areas:
- Pipeline discovery
- Repository security posture management
- Build integrity verification
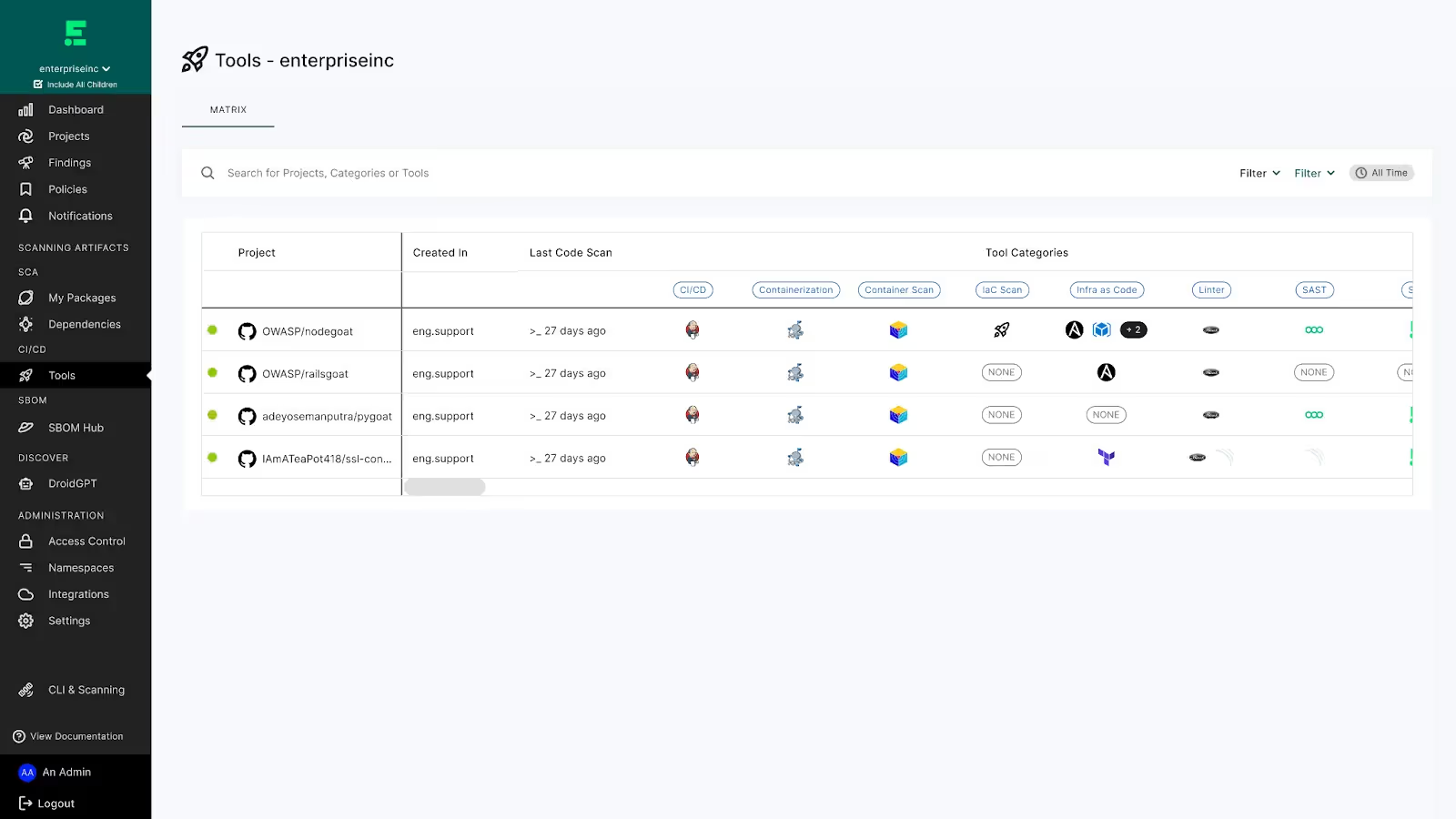
Pipeline Discovery
Reveal shadow engineering and discover everything that touches your code, from the developer’s laptop to build and deployment. Pipeline discovery gives you visibility into the tools developers use in pipelines across your organization, a clear map of your security coverage in those pipelines, and areas of increased risk and policy violations.
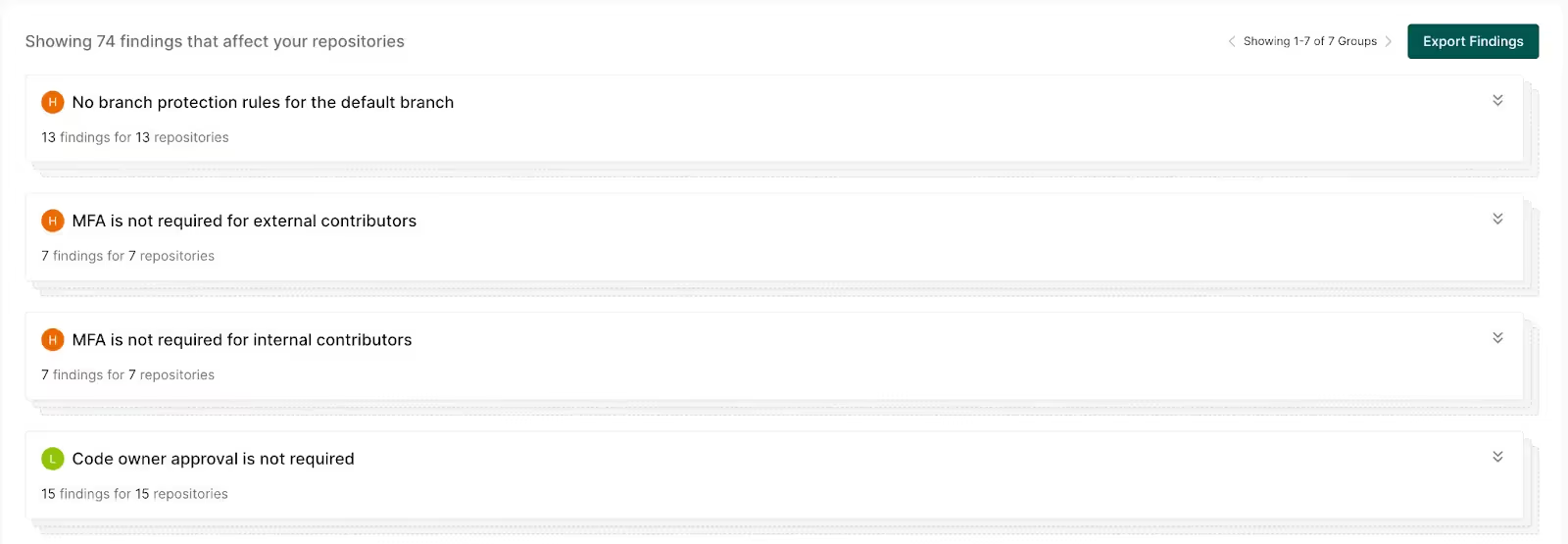
Repository Security Posture Management (RSPM)
With RSPM, you can continuously monitor and strengthen the security posture of source code repositories. Detect repo misconfigurations, best practices, and risks with over 50 out-of-the-box policies. Checks include unprotected branches, missing MFA, overprivileged developer accounts, and more. RSPM keeps you compliant with CIS benchmarks, flags rogue repositories, and defends against advanced supply chain attacks.
Build Integrity Verification (Artifact Signing)
By signing software artifacts and containers with Endor Labs, organizations can ensure the authenticity and integrity of software artifacts, confirming that they were generated by their CI/CD pipelines and have not been tampered with prior to being deployed into production. Endor Labs signs packages and containers with detailed provenance information, including the corresponding source code repository, branch, code commit, and repository owner. This enables operations teams to swiftly and precisely identify the development teams accountable for specific software assets, and developers to accurately pinpoint the version of the source code for a running system, drastically expediting issue triage and remediation.
Learn more in Signing Your Artifacts For Security, Quality, and Compliance and our on-demand webinar, Artifact Signing 101.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:










.avif)