Secrets Detection
Catch exposed secrets at the source
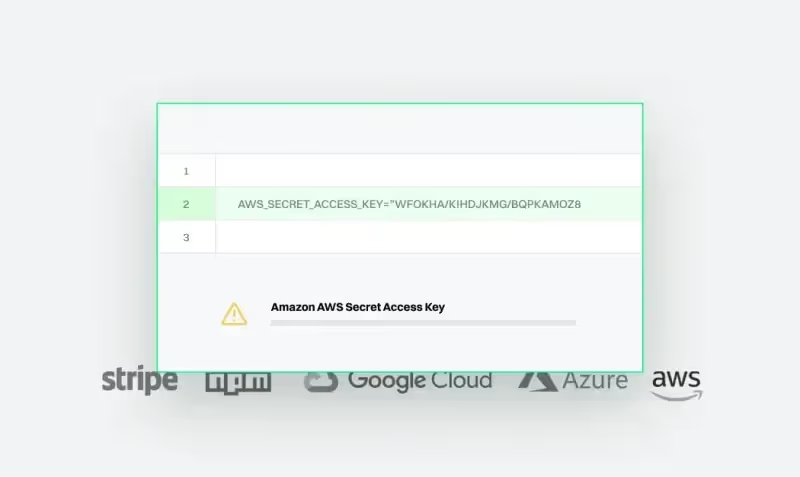
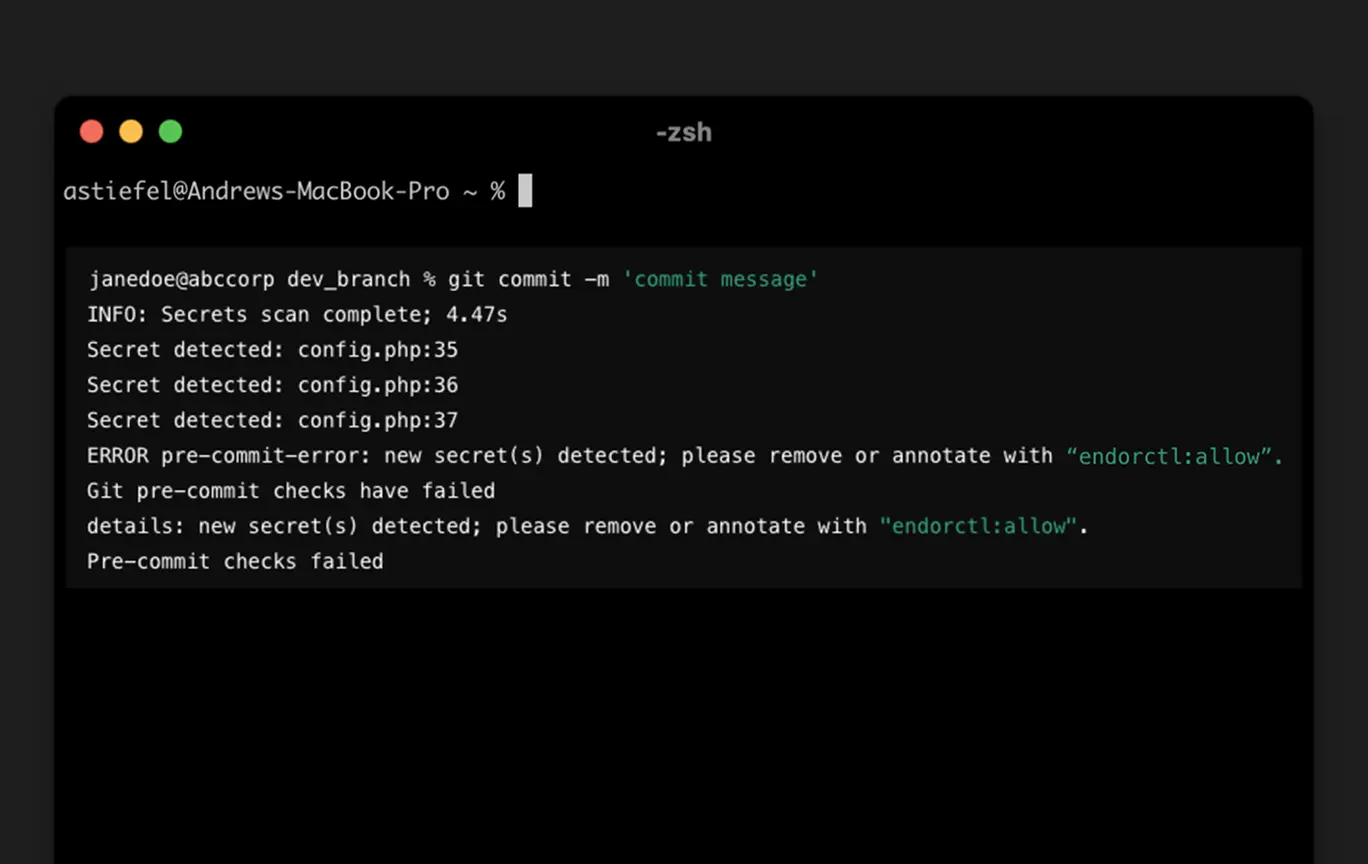
Consolidate secret scanning with SAST and SCA to catch leaked API keys, credentials, and tokens before they reach production.

How it works

1
Detect exposed secrets
Scans code for hardcoded secrets, API keys, and other sensitive data.

2
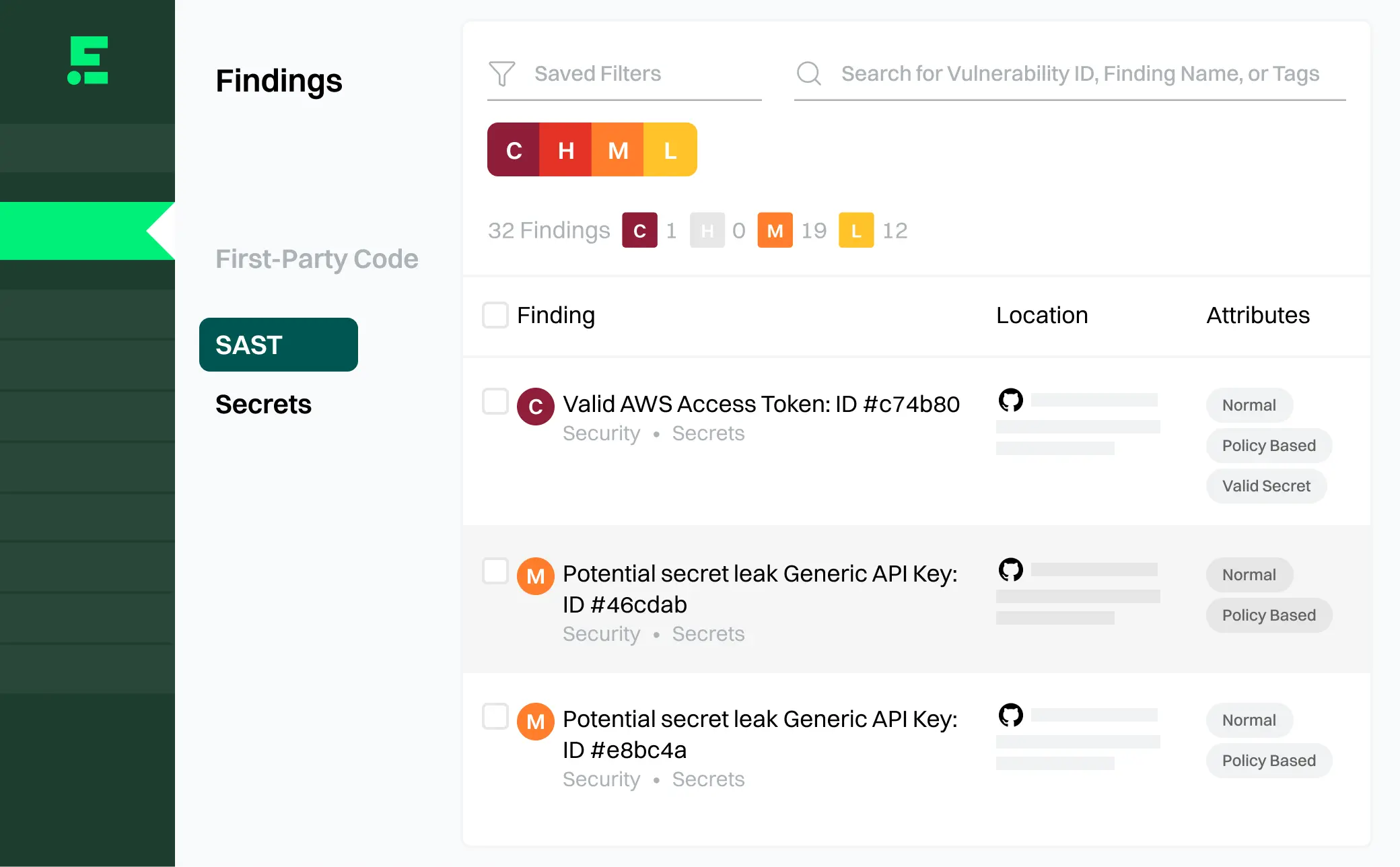
Validate active credentials
Reduce false positives by validating which credentials are active.
Securing code written by humans and AI at:


































































No items found.