This article is part of a 5-part series on secure code prompt patterns.
- Design-Spec Prompt Pattern (this blog)
- Secure vs Insecure Diff Prompt Pattern
- Anti-Pattern Avoidance Prompt Pattern
- Toolchain-Aligned Prompt Pattern (coming soon)
- Test-First Prompt Pattern (coming soon)
AI coding editors like Cursor and GitHub Copilot are rewriting how software gets built. In doing so, they’re reshaping a process that’s been relatively stable for decades: the software development lifecycle (SDLC).
Let’s start with a quick recap. The traditional SDLC follows a predictable flow:
- Planning – Define business goals, scope, stakeholders.
- Requirements – Document functional and non-functional needs.
- Design – Translate needs into architecture and threat models.
- Develop – Write and review code.
- Test – Verify that the code meets its requirements.
- Deploy – Release, monitor, and improve.
This process isn’t going away, but it is evolving. And nowhere is that evolution more dramatic than in the way developers now begin a coding task.
The prompt is now your most important design document
When developers start work in AI code editors, they start with the prompt. The prompt encodes the developer’s understanding of what the software should do (requirements), how it should be built (design), and potential security implications (threat modeling).
This change has big implications for application security. If a developer forgets to mention specific security requirements in the prompt—input validation, authentication, or specific cryptographic practices in the prompt—those requirements are likely to be omitted from code the model generations.
Even when working in the narrow scope of a single file or line of code, AI models won’t generate secure code by default. As a result, the prompt is now your most important design document because it collapses the second and third phases into the code development.
How to write a structured prompt for secure coding
To build secure software in an AI-driven development environment, teams need to treat prompt-writing like they would architecture reviews or threat modeling. That starts with a structure.
Here’s a prompt template you can use to make sure your AI agents generate code that’s secure by design. It maps directly to the core pillars of secure software development:
Most importantly this format doesn’t require developers to become prompt experts—it just gives them a checklist that mirrors how security teams already think.
Example prompt
Here’s what it looks like when everything comes together in a prompt that encodes security, architecture, and business intent:
Prompt: Write a secure Python Flask route that accepts a JSON payload from an authenticated user and inserts it into a PostgreSQL database via SQLAlchemy.
Security requirements: Validate fields to be ≤ 100 characters, allow access only to users with the “admin” role, sanitize error output, and encrypt email and phone number fields at rest.
Avoid CWE-89 (SQL Injection), CWE-79 (XSS), CWE-522 (Insufficient Password Storage).
Environment constraints: Python 3.10, Flask 2.x, SQLAlchemy, running in AWS Lambda.
Output requirements: Complete implementation with docstrings, inline security comments, and accompanying unit tests. No placeholder secrets or hardcoded values.
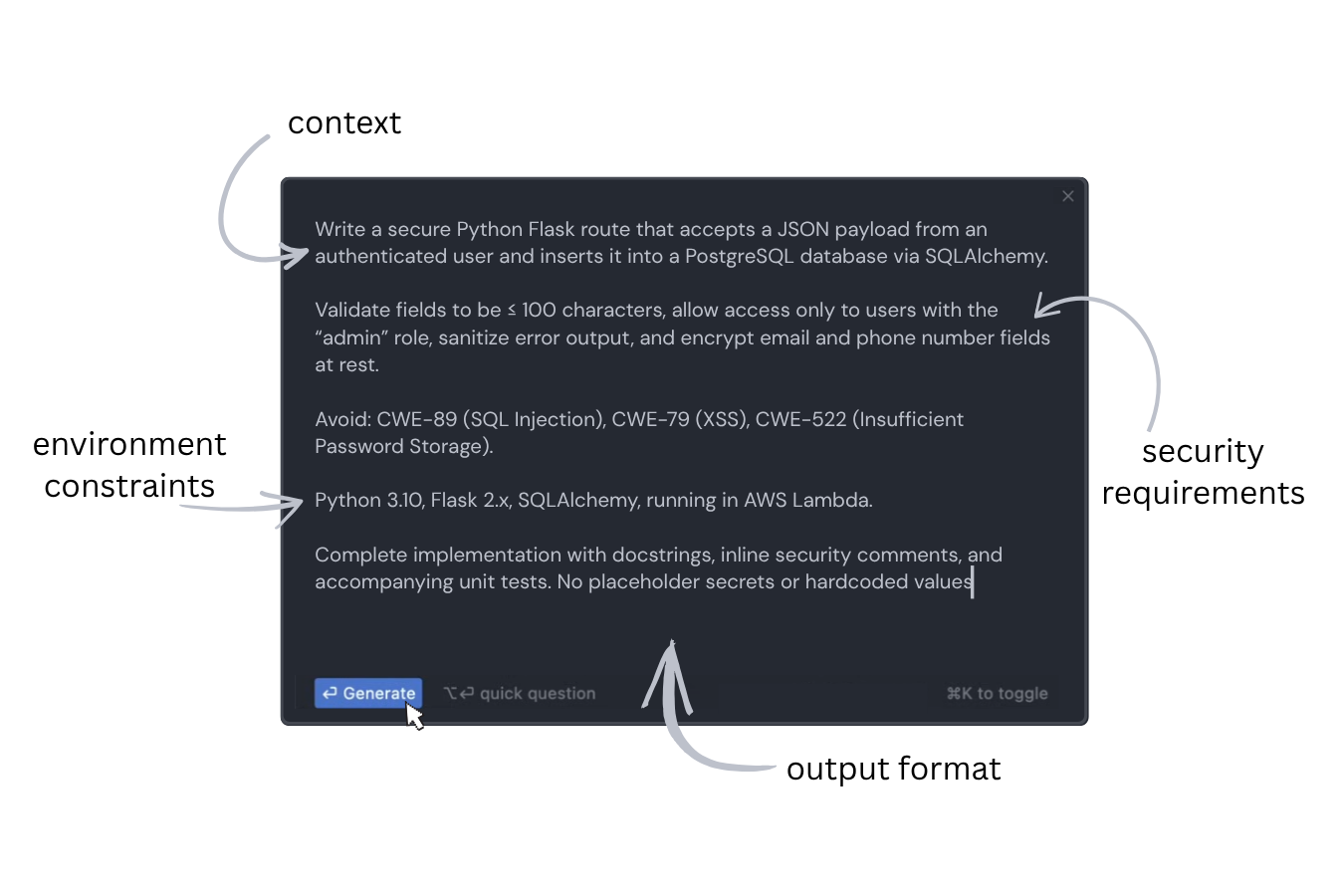
By passing this structured instruction to an AI assistant, a developer skips days of iteration and gets back code that reflects both business needs and security policies—from the start.
Secure by design starts with the prompt
Software development is moving faster than ever, and security has to keep up. As LLM-based agents take on more of the coding burden, we can’t rely on traditional gates that happen after design or review. The only way to shift left in this new reality is to treat the prompt as a design artifact.
By adopting structured prompting practices now, you empower developers to generate code that aligns with your policies, avoids known vulnerabilities, and requires fewer security fixes later.
Get 40+ AI prompts for secure vibe coding here.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:









.avif)
