Mobile apps present distinct security challenges compared to desktop software due to their integration with diverse operating systems, hardware configurations, and constant connectivity. Unlike desktop applications, they must safeguard user data across various platforms and defend against numerous potential attack vectors while ensuring smooth user experiences.
Gaming companies with mobile versions must specifically prioritize data protection and implement robust security measures to ensure a safe and secure gaming experience for their players. While the dominant languages in the mobile development space (Kotlin for Android, Swift for iOS) behave differently, there is one constant across all application development: Roughly 80% of code in modern applications is open source software (OSS). This makes OSS the largest attack vector for most applications, which is why selecting safe OSS packages and prioritizing risks is crucial.
First let’s take a look at Android development.
Threat Landscape for Android Development
Android Security Bulletin (ASB) publishes a monthly update that classifies security vulnerabilities into five buckets, however ASB focusses majorly on platform fixes, linux kernel fixes and system of chip issues.
- Remote code execution (RCE)
- Elevation of privilege (EoP)
- Information disclosure (ID)
- Denial of service (DoS)
- Classification not available
Meanwhile OWASP has a more exhaustive classification of Top 10 Mobile risks that was updated in 2023. As our focus is on risks introduced by application-level code in OSS dependencies, we’ll take a look at specific risks in that space.
Examples of Vulnerabilities in Popular Open Source Kotlin and Android Libraries
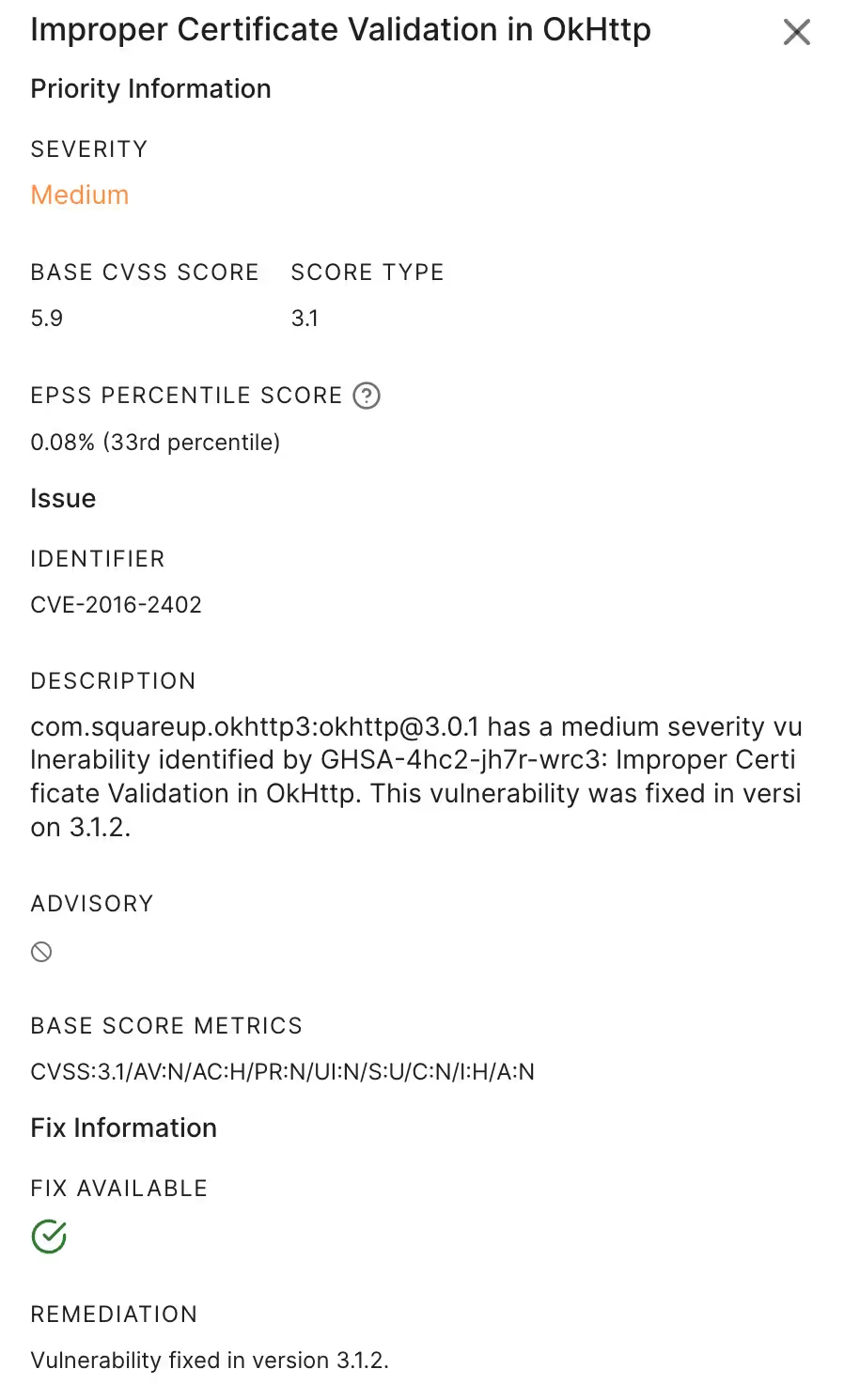
OkHttp
CVE-2016-2402 - GitHub Advisory Database
Certificate pinning is a security measure utilized to counteract Man-In-The-Middle (MITM) attacks perpetrated by malicious entities with privileged access. These adversaries are presumed to possess the private key used to sign a certificate, thereby gaining the trust of the system hosting the targeted application.
The foundation for many networking operations, OkHttp offers an efficient way to make HTTP / HTTP2 requests and is popular among the dev community for its ease of use. However versions <= 2.7.3 and / or >= 3.0.0, <= 3.1.1 of OkHttp library would make it possible for malicious actors to exploit this weakness and consequently defeat the purpose of certificate pinning.
The aforementioned versions of OkHttp library did not validate that the pinned certificate was in the chain to a trusted authority, thereby rendering pinning ineffective as a safeguard.
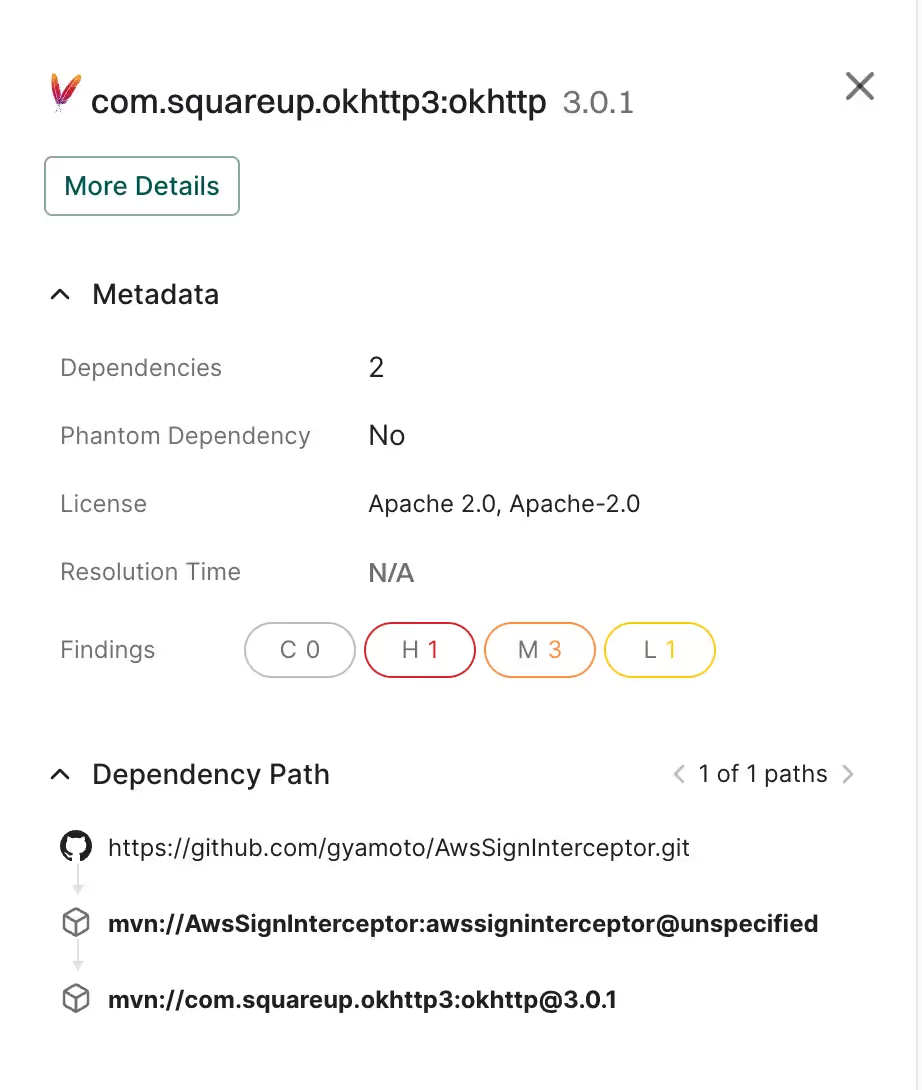
For example, if a project did have one of the vulnerable version ranges as a dependency we would see findings reported accordingly, along with highlighting how the vulnerable dependency was brought in.
Bouncy Castle
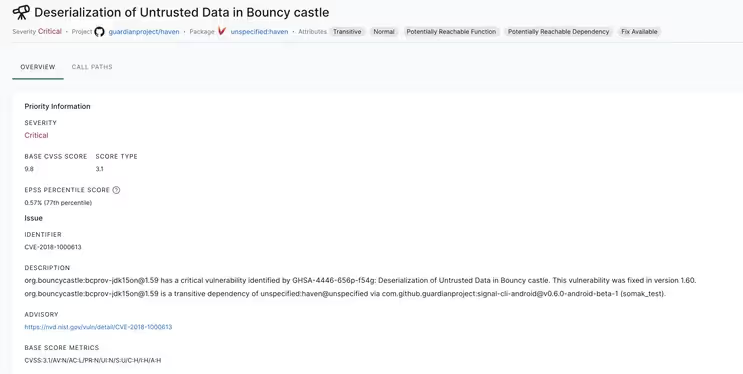
CVE-2018-1000613 - GitHub Advisory Database
Transport Layer Security (TLS) is a mechanism for secure transport over network connections. TLS may utilize RSA cryptography to secure the connection, and implementations that don't closely follow the descriptions in RFC 5246 may leak information to an attacker when they handle PKCS #1 v1.5 padding errors in ways that lets the attacker distinguish between valid and invalid messages.
An attacker may utilize discrepancies in TLS error messages to obtain the pre-master secret private RSA key used by TLS to decrypt sensitive data. This type of attack has become known as a Bleichenbacher attack.
BouncyCastle is a popular library for the secure implementation of cryptographic algorithms in Java applications. It is based on the Bouncy Castle Cryptography Package for Java, which is a comprehensive suite of FIPS-certified cryptographic algorithms. The library provides a simple API that allows developers to easily add encryption and decryption functions to their applications with little or no knowledge of cryptography. The library also provides support for digital signature generation and verification, as well as for securely managing and working with key stores and certificates.
Prior to version 1.0.3, when configured to use the JCE (Java Cryptography Extension) for cryptographic functions, BouncyCastle TLS provided a weak Bleichenbacher oracle when any TLS cipher suite using RSA key exchange is negotiated. An attacker can recover the private key from a vulnerable application. This vulnerability is referred to as "ROBOT."
Taking an example of guardianproject/haven project, we can see the said vulnerability being reported:
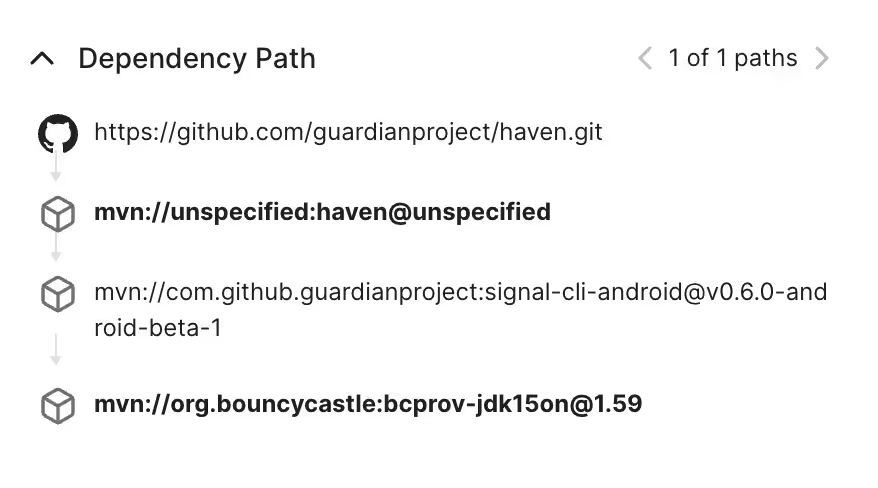
Bouncy castle is not a direct dependency but is transitively added to the project via dependency on signal-cli-android dependency, which is something that is highlighted in the below dependency path.
Function-Level Reachability for Kotlin with Endor Labs
Software Composition Analysis (SCA) with Endor Labs is all about accurate, low-noise results, that are based on context. Context can come in many forms: Is this a dependency? How many projects is it used in? What’s the EPSS score for a given vulnerability? Is this risk in a direct or transitive dependency?
For languages with a high volume of potential vulnerabilities, one of the most important pieces of context is reachability. Can this risk actually impact my application? Kotlin now joins several other languages (including Python, Go, and Java) with function-level reachability analysis on Endor Labs.
Kotlin is compatible with Java and can be compiled to run on the JVM. However, the Kotlin compiler can also target a native backend or a JavaScript backend. Regardless of the target of your Kotlin project, we can perform reachability analysis because we understand your Kotlin project at the code level.
Let’s take an example project, a Reddit client for Android, which when built with the gradle assemble command produces an .apk file. Scanning this with Endor Labs shows 40 findings of varying severity:
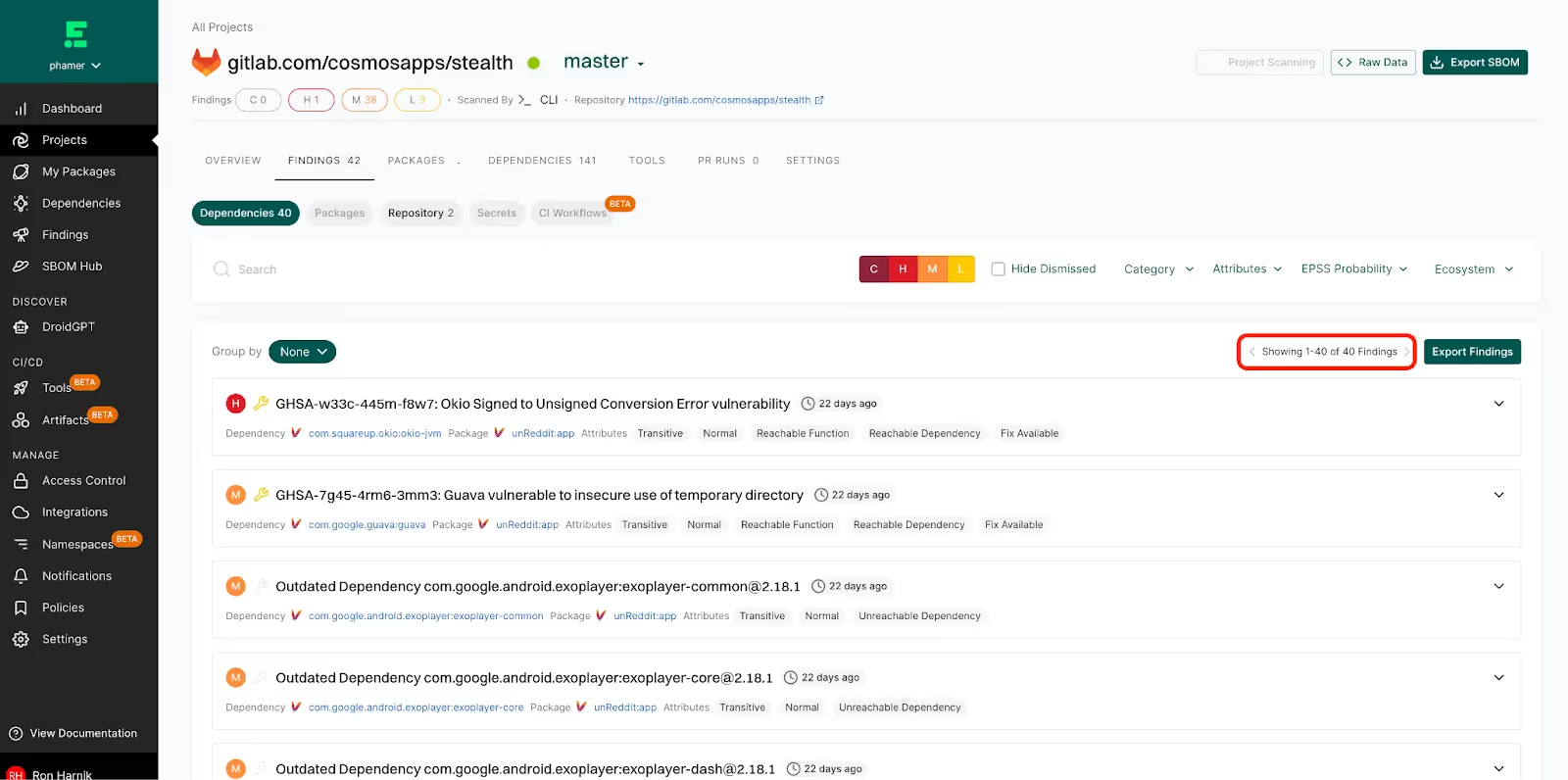
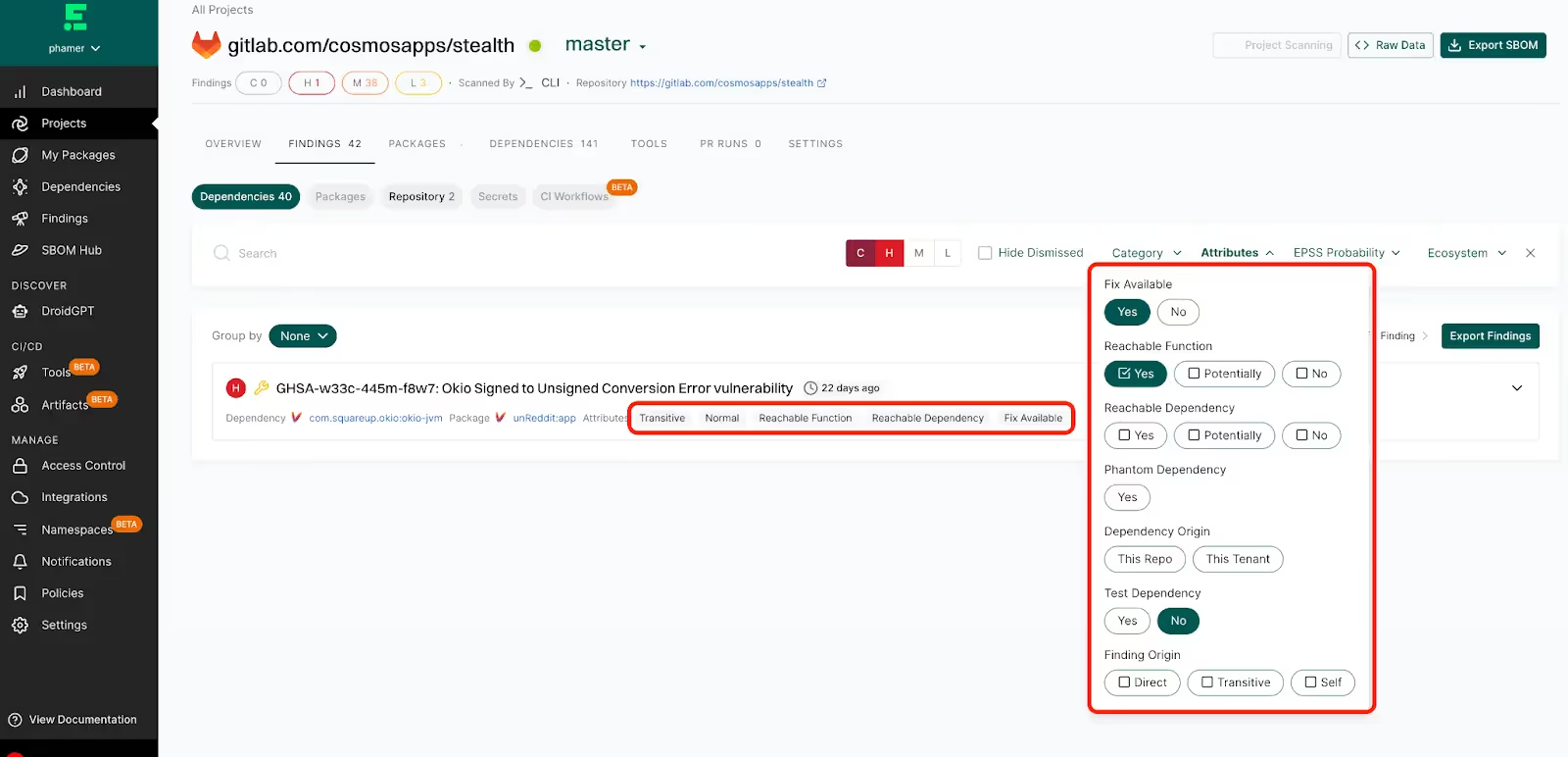
We can add several layers of context to help you decide which findings need to be prioritized for immediate action. In this case, we add three filters (function-reachable vulnerabilities, fix available, and a critical or high severity) and end up with a single vulnerability:
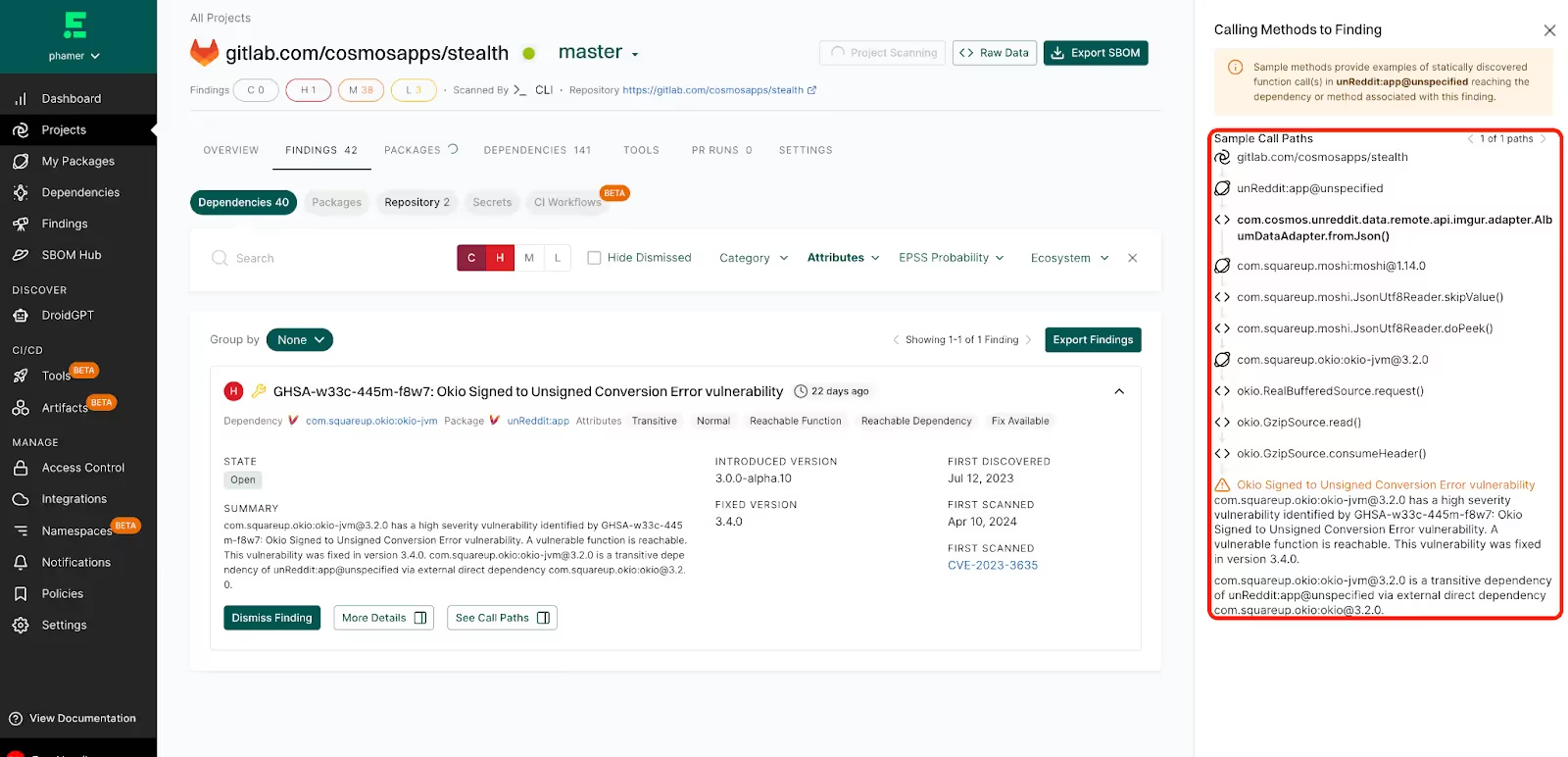
When we open the finding, we can also see the call path from our 1st party code to the vulnerable function, giving us all the evidence we need to prioritize the fix:
What about Swift and iOS apps?
The Swift ecosystem is not immune to vulnerabilities, just like any other ecosystem. There are various risks that can compromise the integrity of an iOS app, from Denial of Service to unpatched security flaws. Some of the common vulnerabilities include HTTP/2 Rapid Reset Attack, Path Traversal, and Arbitrary Code Execution.
HTTP/2 Rapid Reset Attack
Attackers can exploit flaws in the HTTP/2 protocol, specifically related to the handling of connection resets, to disrupt game server communication and launch denial-of-service (DoS) attacks. By rapidly resetting HTTP/2 connections, attackers can overwhelm game servers, causing them to become unresponsive and disrupting gameplay for players.
Path Traversal
Attackers can exploit the path traversal vulnerability in ZIPFoundation to access files or directories outside the intended directory structure. This can lead to unauthorized access, data loss, or system compromise. In the context of a game developed in Swift, this vulnerability could result in game crashes, data corruption, or unauthorized access to sensitive resources.
Arbitrary Code Execution
This vulnerability allows attackers to execute arbitrary commands or code on a target system, potentially leading to unauthorized access, data breaches, or system compromise. CVE-2019-8849 is a vulnerability that affects applications utilizing SwiftNIO, a low-level networking framework for building high-performance, event-driven applications in Swift. Specifically, this vulnerability pertains to applications employing Transport Layer Security (TLS) for secure communication over the network.
Protecting iOS Applications with Endor Labs
Endor Labs supports SCA for Swift and Objective-C using the CocoaPods package manager. Like with all supported languages, Endor Labs goes beyond security risks and detects license risk, and operational issues such as outdated or unmaintained dependencies, in direct or transitive dependencies:
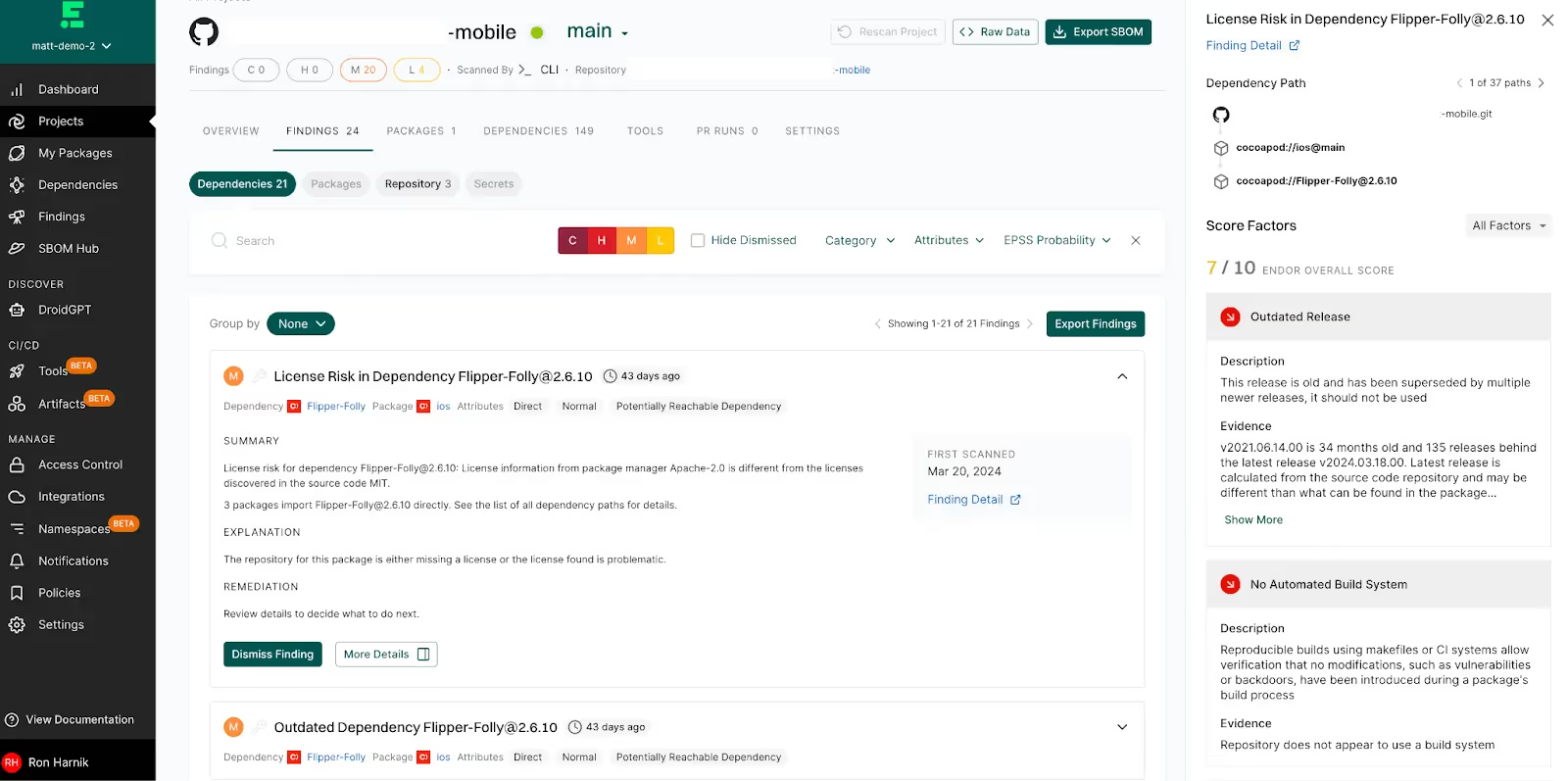
The Swift ecosystem is known as a relatively secure environment, with only around 30 known vulnerabilities compared to other ecosystems that have thousands. As a result, reachability analysis doesn’t add significant context in this ecosystem (while score factors do). The low number of vulnerabilities provides developers and security professionals with more time to prioritize their efforts and improve security measures without being overwhelmed by a large number of vulnerabilities. This is also why we’ve chosen to prioritize function-level reachability analysis for languages with higher risk volumes.
The Endor Labs Software Supply Chain Security Platform
To get started with Endor Labs, start a free 30-day trial or contact us to discuss your use cases.
Select Better Open Source Software
Select better open source dependencies with 150+ checks and scoring based on security, legal, popularity, activity, and quality. Defend against OWASP OSS Top 10 Risks [LINK] such as typosquatting, malicious and abandoned dependencies.
Prioritize Open Source Vulnerabilities (SCA)
Cut over 90% of vulnerability noise with function-level reachability analysis across both direct and transitive dependencies. Codify highly customizable policies to provide developers feedback in PR comments, break builds in CI, or simplify notify them via Jira tickets.
Secure Repositories and CI/CD Pipelines
Gain visibility into security tool coverage across your CI/CD pipelines and continuously monitor the security posture of source code repositories. Detect repo and GitHub Actions misconfigurations, best practices, and risks with over 50 out-of-the-box policies, including coverage for CIS best practices for GitHub.
Trust What You Ship with Artifact Signing
Ensure the authenticity of software artifacts with a single GitHub action. Artifact signing is a hassle-free alternative to Sigstore that confirms code provenance and lack of tampering. Cryptographic artifact signatures are a powerful tool to enable strong admission control and traceability to support effective security, quality, and compliance programs.
Ensure compliance across the SDLC
Detect legal and licensing risk, and centrally create, manage, and analyze SBOM & VEX. Prioritize applicable vulnerabilities for PCI-DSS and FedRamp and accelerate compliance with CIS, NIST, SSDF, SLSA, EO 14028, and more.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:












