Pipeline and Workflows Discovery
Get visibility into tools and GitHub Actions used in your CI, understand security coverage and risks, and find policy violations.
Repo Security Posture Management
Detect repo misconfigurations, best practices, and risks with over 50 out-of-the-box policies.
Build Integrity Verification
Ensure the authenticity of software artifacts, confirming their source and that they have not been tampered with.

Trusted by Leading Teams


































































Find pipeline security coverage gaps.
Shadow engineering is on the rise
Developers are incentivized to leverage automated tools that help them ship faster. These can be third-party extensions, CI/CD tools, or other apps found on Source Code Management (SCM) marketplaces, such as the GitHub marketplace. Like in the early days of cloud, this has tremendous value in terms of agility but also introduces the challenge of shadow engineering. This is when developers create unofficial, rogue repositories or use unsanctioned or misconfigured tools and processes that don’t adhere to the organization's best practices and often escape the scrutiny of security protocols. This lack of visibility and control can result in unknown vulnerabilities and malware, compromise code integrity, and create compliance issues.
Get full visibility with pipeline discovery
Endor Labs CI/CD automatically discovers everything that touches your code, from your source code management system, to build, test and deployment. Pipeline discovery gives you visibility into the tools developers use in pipelines across your organization, and gives you a clear map of your security coverage in those pipelines - see exactly which CI/CD, SCA, SAST, Container Scan, IaC and other tools are used, and where insecure gaps exist.
Treat CI workflows as dependencies.
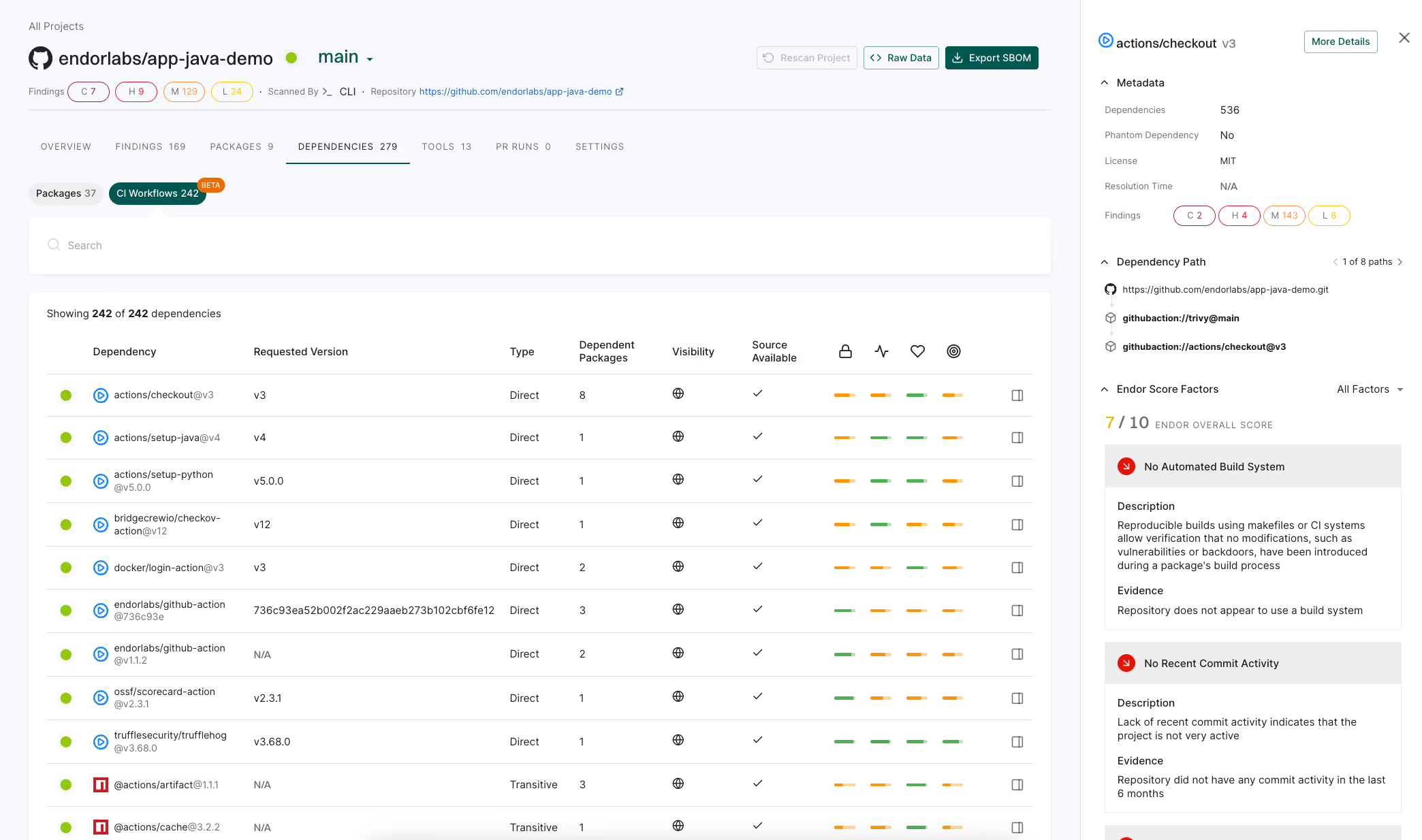
Are your GitHub Actions risky?
Pre-built GitHub Actions are a huge accelerator for DevOps, as they allow you to gain all the benefits of code reuse for your CI/CD pipelines. Many of these Actions are open source projects, and so the Actions ecosystem has all of the advantages — and challenges — of open source dependency management. We might be used to thinking of “dependencies” as the libraries that become part of our applications, but the tools we use to build and test our applications are dependencies (and part of our supply chain) too. And since Actions are a sort of application component (often written in TypeScript or JavaScript, but can also be deployed as Docker images containing any code the authors want), they even have their own open source library dependencies. And just like any kind of dependency we have, we need visibility and a system for identifying and prioritizing risks.
GitHub Actions Security
Endor Labs' groundbreaking Actions risk analysis feature empowers organizations to enumerate actions and their dependencies effectively. By surfacing known vulnerabilities, excessive permissions, and configuration issues, Endor Labs enables informed actions choices, supported by EndorScore, dependency trees, and risk enumeration. Together, these capabilities allow you to reduce the time to research actions before adopting them, prompt surface important risks that require updates or mitigation actions, and ensure that you have confidence in your whole chain of dependency when you do adopt an action.
- Detect Malware and Vulnerabilities in CI Dependencies: Quickly discover if vulnerable or malicious software is part of your CI environment.
- Prevent Breaking Changes in CI by Pinning of GitHub Actions: Reduce breaking changes and supply chain risk by ensuring the code your workflows run doesn’t change without your knowledge.
- Prevent Unauthorized Modification of CI Pipelines: Identify code injection risks in your CI pipelines that could be used to steal information or change the outcome of a pipeline. (poisoned pipelines in owasp top 10)
- Visibility into the GitHub Actions You Use: Understand the impact of known or headline incidents with visibility into the actions your CI environment depends on.
Detect misconfigured repositories.
Are my pipelines secure?
Security tools, such as SAST, SCA, IaC, and Secret scanners, are a necessity to protect the SSCS. In addition to selecting the best tools for the job, the way they’re integrated into pipelines is also critical. Even the best of tools can be disruptive to development workflows when they aren’t implemented and managed effectively. And depending on organization size, there may even be some uncertainty about which tools are in which pipelines. The first step towards an effective management strategy is visibility: The ability to see what tools are deployed across each code repository and CI/CD pipeline.
Repository Security Posture Management (RSPM)
With RSPM, you can continuously monitor and strengthen the security posture of source code repositories. Detect repo misconfigurations, best practices, and risks with over 50 out-of-the-box policies. Checks include unprotected branches, missing MFA, overprivileged developer accounts, and more. After gaining visibility into all pipelines, RSPM helps you harden those pipelines and repositories with policies that find exploitable misconfigurations. The out-of-the-box policies cover the CIS Benchmark for GitHub and many additional best practices.

Verify the integrity of every build.
Can I trust what I ship?
If you don't know where your software comes from, it can expose you to hidden risks. Without continuous identity checks and strong safety measures for keys and secrets, your software artifacts could be vulnerable to breaches, attacks, exploitation and other software supply chain risks. How can we ensure that code was not manipulated in the build pipeline? And how can we do it without the tax of implementing complex signing schemes?
Code provenance
By signing software artifacts and containers with Endor Labs, organizations can ensure the authenticity and integrity of software artifacts, confirming that they were generated by their CI/CD pipelines and have not been tampered with prior to being deployed into production. Endor Labs signs packages and containers with detailed provenance information, including the corresponding source code repository, branch, code commit, and repository owner. This enables operations teams to swiftly and precisely identify the development teams accountable for specific software assets, and developers to accurately pinpoint the version of the source code for a running system, drastically expediting issue triage and remediation.
Read more in Signing Your Artifacts For Security, Quality, and Compliance.
The economic impact of OSS risk prioritization



