If you're evaluating alternatives to Snyk, you're not alone. Despite being one of the most widely adopted application security platforms, many teams hit friction as their programs scale and modernize. The noise becomes harder to manage. Developers push back on alert fatigue. And the security team finds itself spending more time triaging findings than actually reducing risk.
According to G2 reviews, false positives are consistently cited as a top pain point with Snyk, with users reporting that "there are a lot of false positives that need to be identified and separated." When your developers are drowning in tickets for vulnerabilities they can't fix—or worse, vulnerabilities that aren't actually exploitable in their code—trust breaks down fast.
This guide covers seven Snyk alternatives across different categories: developer-friendly application security platforms, open source tools, freemium solutions, and specialized options for runtime security and cloud teams. We'll examine what each option does well, where it falls short, and who should consider it.
Why teams switch from Snyk
Before exploring alternatives, it's essential to understand the common patterns that drive teams to evaluate other application security tools.
1. Alert fatigue kills productivity and morale
Snyk's approach to vulnerability scanning tends to surface every theoretical risk without adequate context about exploitability. For a typical engineering organization, this translates to thousands of findings, most of which aren't actually reachable by user input or executable in production. Once found, without enough context, security teams end up needing to manually research each vulnerability to determine if it's real, while developers get annoyed but learn to ignore the noise.
The impact? According to customer reports we've seen at Endor Labs, organizations switching away from Snyk have reduced their monthly security tickets by up to 95%—from 2,600 findings down to 146 actionable issues in minutes. That's not a marginal improvement. That's the difference between a security program that supports strong revenue generation and developers respect and one they route to spam.
2. Coverage is incomplete, especially for complex build systems
If you're using Bazel, monorepos, or C/C++ codebases, Snyk's coverage becomes noticeably thinner. Results differ between the CLI and SCM integrations, creating confusion between security and engineering about which findings are real. The combination of silent failures, gaps in coverage, and inaccurate results wastes time on false positives and misses real vulnerabilities, eroding trust.
3. The AI promise doesn't match the product
Snyk has rebranded heavily around AI capabilities, but many of those features remain roadmap items rather than production capabilities. Teams expecting mature AI-driven analysis, particularly for AI model discovery and governance, find gaps between the marketing narrative and what's actually shipped. For example, as Snyk still hasn’t shipped AI-native capabilities like AI model discovery, prompt injection security, and other features in their core platform.
Top 7 Snyk alternatives for 2026
This guide covers seven categories of Snyk alternatives, from enterprise platforms to open source tools. We'll look at what each option does well, where it falls short, and who should consider it.
- Developer-friendly alternative: Endor Labs
- Open source alternatives: Opengrep, Syft, and Trivy
- Freemium alternative: GitHub Advanced Security
- Open core alternative: Semgrep
- Runtime alternative: Upwind
- Cloud teams alternative: Wiz Code
- Small teams alternative: Aikido Security
Detailed comparison of Snyk alternatives
1. Best developer-friendly Snyk alternative: Endor Labs
If you're looking for a platform specifically designed to solve Snyk's core limitations—noise, shallow reachability, and poor developer experience—Endor Labs is purpose-built to deliver that.
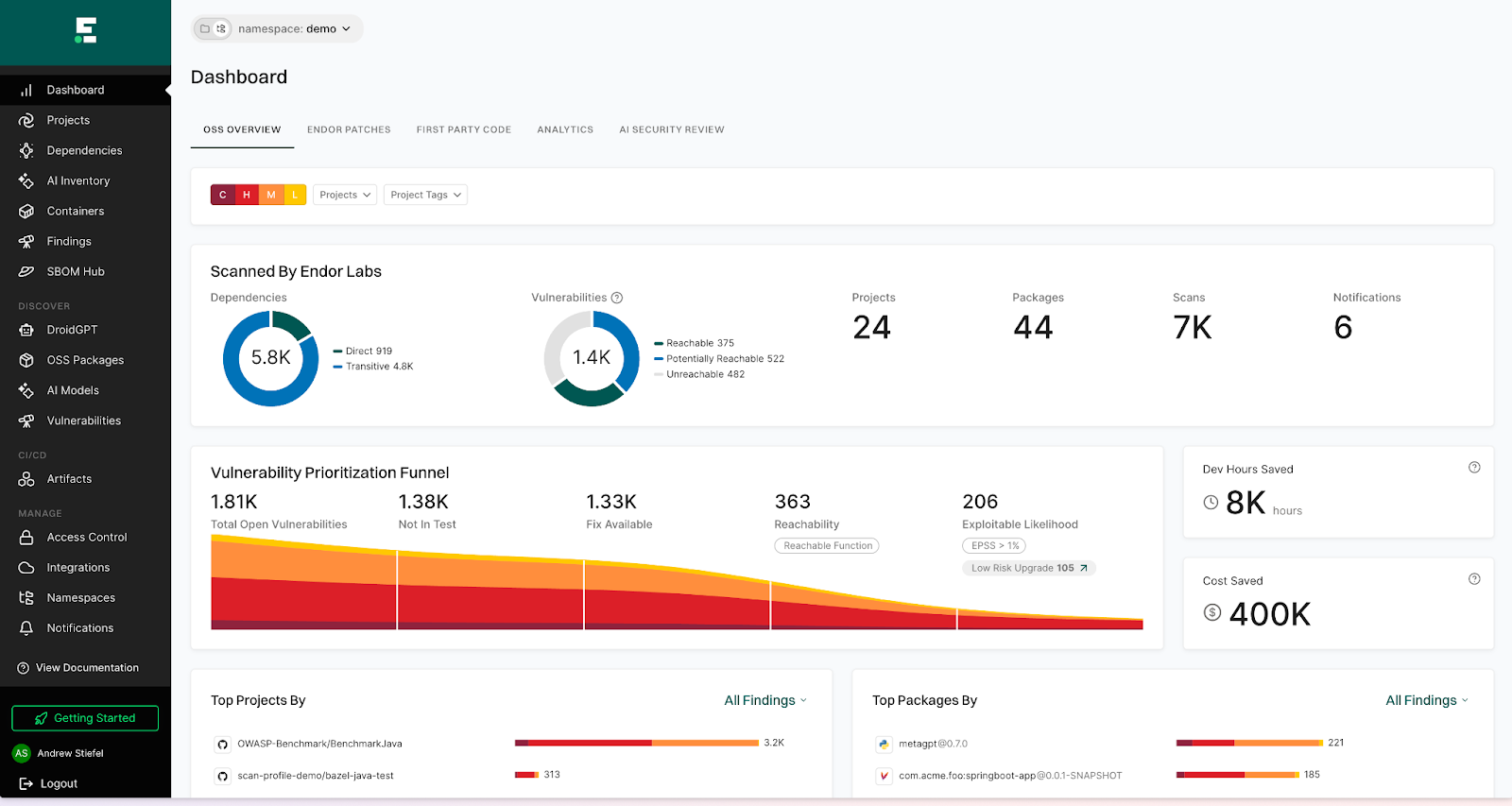
What makes Endor Labs different
Endor Labs is architecturally AI-native, not AI-retrofitted. The platform provides function-level reachability analysis across code, open source dependencies, and containers. This means it can tell you whether vulnerable code is actually called by your application, dramatically reducing false positives.
The reachability extends through the entire dependency graph, including transitive dependencies. So when a critical vulnerability appears in a package six layers deep, Endor Labs can determine if your code ever reaches that function—and if it doesn't, you're not wasting engineering time on theoretical risks.
Full coverage across code, secrets, open source dependencies, containers, and CI/CD security
The Endor Labs application security platform includes SAST, SCA, secrets detection, malicious package detection, and container scanning in a unified experience. For AI governance, it provides AI-BOM and AI-SPM capabilities that discover and inventory every AI model and service in your applications, then assess security, licensing, and compliance risks.
The AI capabilities extend to code review. Endor Labs’ AI SAST uses multiple specialized AI agents working together to analyze code context, achieving a 95% false positive reduction through intelligent triage and prioritization. These agents understand your codebase and business context, not just pattern matching.
Developer experience that actually works
Endor Labs provides clear evidence directly in pull requests and IDEs. No context switching. No vague descriptions. When a vulnerability matters, developers see exactly why it matters, where it's reachable, and how to fix it. The platform includes upgrade impact analysis to identify breaking changes before suggesting fixes, plus automated patches for hard-to-fix libraries when version upgrades aren't safe.
Organizations like Atlassian, Cursor, and OpenAI have switched to Endor Labs to reduce noise and rebuild developer trust in their application security programs.
Endor Labs limitations
Endor Labs is an enterprise platform, which means it's built for organizations with larger engineering teams, typically more than 50 developers. If you're a three-person startup, the investment probably doesn't make sense yet. The platform also focuses deeply on AI/ML and static analysis approaches over other domains like DAST.
Who should consider Endor Labs
- High-velocity or scaled engineering organizations who are tired of noise
- Companies using Bazel, C/C++, or complex build systems that need complete coverage
- Teams building AI-native applications who need real AI governance today, not next year
- Security programs that have lost developer trust and need to rebuild it with accurate, actionable findings
2. Open source Snyk alternatives: Opengrep, Syft, Trivy
If you're comfortable with command-line tools and have engineering resources to build your own security workflows, open source tools can provide the scanning capabilities without vendor lock-in.
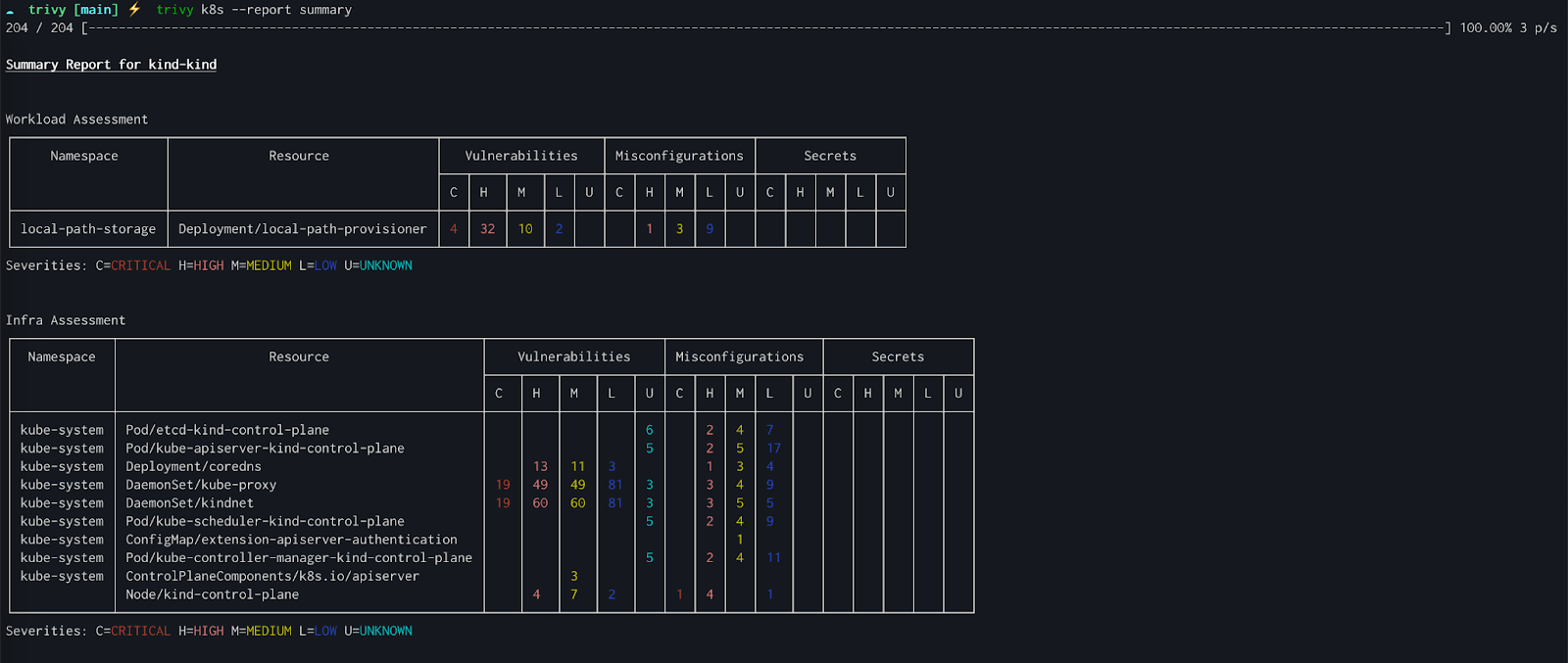
What it includes
- Opengrep is a fork of Semgrep's open source SAST engine, focusing on pattern-based static analysis. It's fast and supports a wide range of languages.
- Syft generates software bill of materials (SBOM) and identifies dependencies in container images and filesystems.
- Trivy is a comprehensive scanner covering vulnerabilities in containers, Kubernetes, IaC, and code.
These tools are powerful individually. They're actively maintained. And they cost nothing.
But here's the catch. Open source tools require significant investment to operationalize. You need to maintain rule sets, tune for false positives, build integrations with your CI/CD pipelines, and create dashboards for visibility. There's no central console, no unified policy engine, and no automatic correlation of findings across different tools.
The noise problem doesn't go away—it actually gets worse because each tool generates findings independently with no shared context. Your security team becomes the integration layer, manually triaging and prioritizing across multiple sources of truth.
Who should consider it
- Small engineering teams with dedicated security engineering resources
- Organizations with strict open source requirements
- Companies building custom security platforms and comfortable investing engineering time in tooling
3. Freemium Snyk alternative: GitHub Advanced Security
If your organization already uses GitHub Enterprise, GitHub Advanced Security (GHAS) provides built-in security scanning without introducing another vendor.
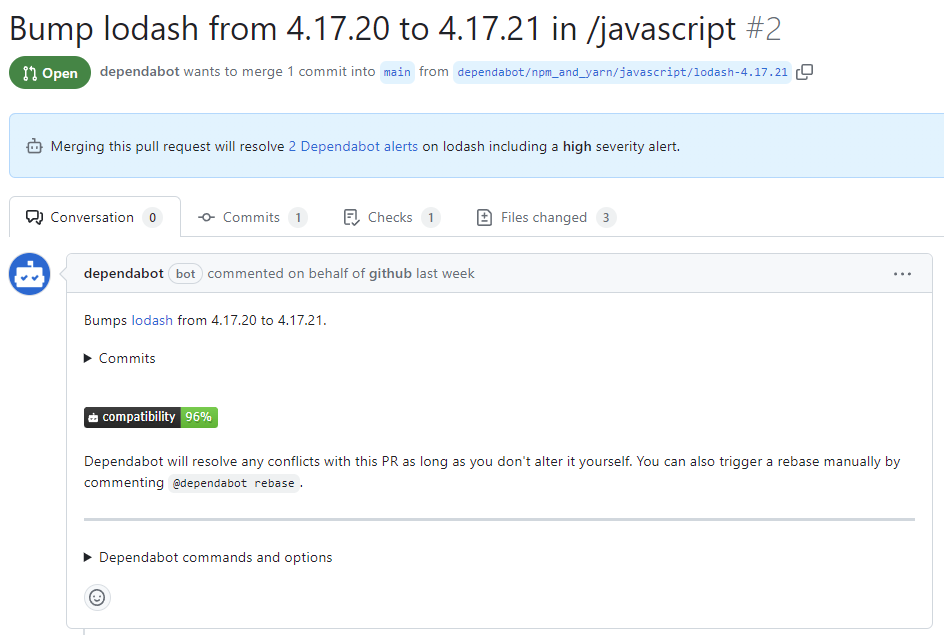
What it includes
GHAS offers CodeQL for SAST, Dependabot for SCA, and secret scanning. The tight integration with GitHub means developers see security alerts in their natural workflow—pull requests, the security tab, code scanning results right where they're already working.
The advantage is simplicity. No separate login, no new interface to learn, no additional tool in the stack. For teams deeply embedded in GitHub's ecosystem, that reduces friction significantly.
Limitations
Like many scanning tools, GHAS can be noisy. CodeQL generates findings based on taint analysis, but without sophisticated reachability analysis, you'll see alerts for code paths that aren't actually exploitable. Dependabot alerts on every vulnerable dependency, regardless of whether your code uses the affected functions.
The platform is also limited to GitHub repositories. If you use GitLab, Bitbucket, or multiple source control systems, GHAS won't cover your entire codebase. And the secret scanning, while functional, lacks the depth and validation capabilities of dedicated secrets management tools.
Who should consider it
- Teams standardized on GitHub Enterprise with security budgets to match
- Organizations looking for good-enough security scanning without adding vendor complexity
- Companies where the GitHub integration is more valuable than best-in-class accuracy
4. Open core Snyk alternative: Semgrep
Semgrep offers an interesting middle ground—open source SAST with a commercial platform layer for teams that need additional capabilities.
What Semgrep does well
The open source engine is excellent for custom rule writing. If your security team has specific patterns they need to detect—proprietary frameworks, internal libraries, company-specific anti-patterns—Semgrep makes it relatively straightforward to write rules. The Pro tier adds managed rules, prioritization, and some remediation capabilities.
For SCA, Semgrep offers reachability analysis, but only for direct dependencies. The analysis doesn't extend to transitive dependencies, which is where most vulnerabilities actually hide in modern applications. If you have a deep dependency tree, you're back to triaging theoretical risks several layers removed from your code.
Limitations
SAST requires extensive rule writing to be effective. Out-of-the-box rules catch common patterns, but achieving low false positives while maintaining coverage means investing significant time in rule development and tuning. The platform isn't AI-native, so you're working with static rules rather than adaptive analysis.
Container scanning is missing entirely. If you're deploying containerized applications—and in 2026, most teams are—you need another tool for that coverage. This creates the same multi-tool fragmentation problem you're trying to escape.
Who should consider it
- Security teams with engineering resources for rule development
- Organizations that need deep customization for proprietary code patterns
- Companies comfortable with a multi-tool stack where Semgrep handles SAST while other tools cover containers and infrastructure
5. Runtime Snyk alternative: Upwind
If your primary concern is understanding which vulnerabilities are actually exploitable in production—not just present in your codebase—Upwind takes a fundamentally different approach by focusing on runtime analysis.
What it includes
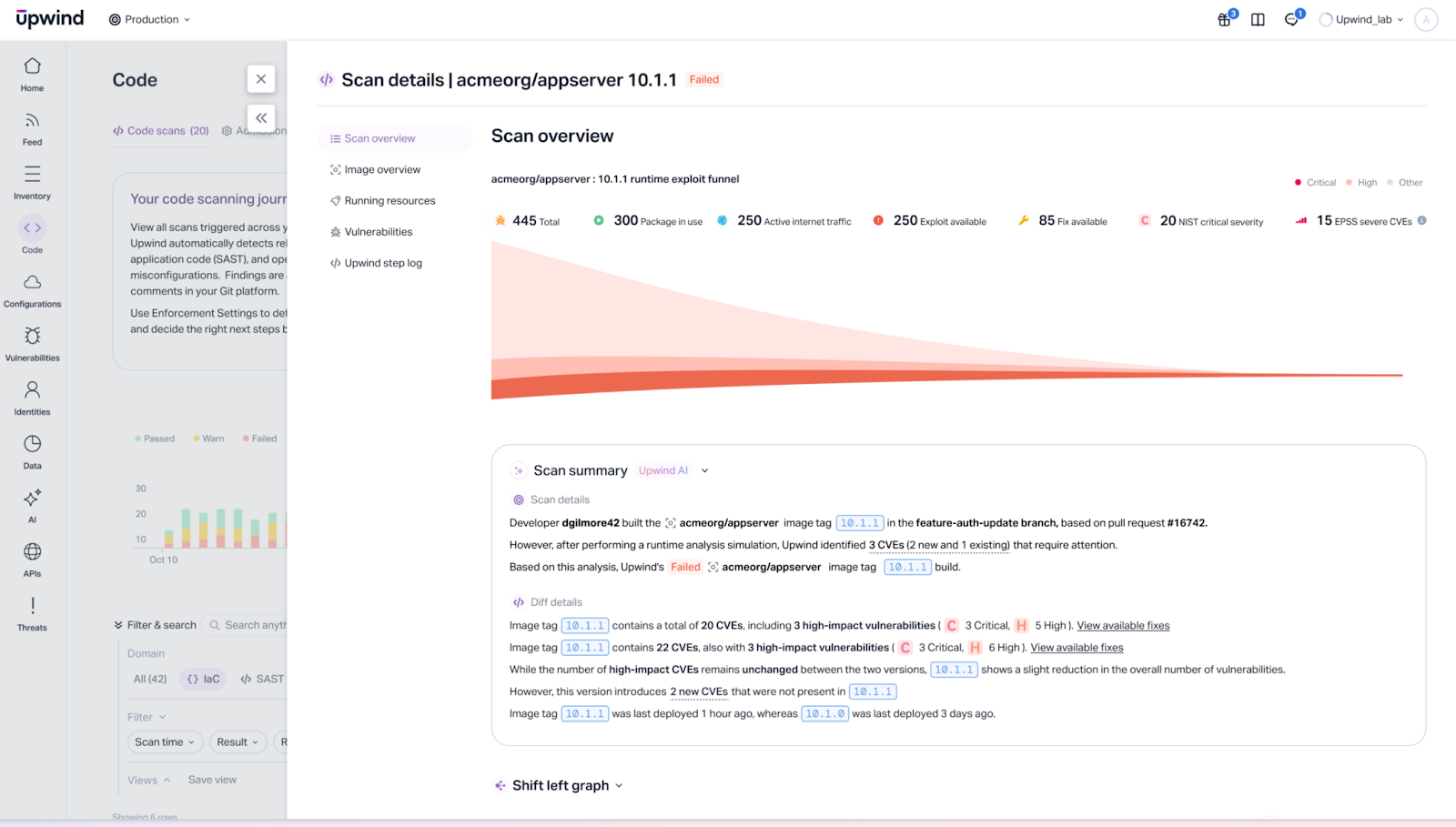
Upwind monitors your applications in production using eBPF-based instrumentation to observe which code paths execute, which libraries get loaded, and which functions actually run. This runtime visibility lets the platform identify vulnerabilities that matter because they're genuinely reachable through real user traffic, not just theoretically present in your dependency tree.
The advantage is clear signal. If a vulnerable function never executes in production, Upwind deprioritizes it. If your application loads a library but never calls the vulnerable code path, you don't waste time on it. This reduces noise by focusing on demonstrated exploitability rather than theoretical risk.
Upwind provides runtime SCA, secrets detection, and attack detection capabilities. The platform can identify when attackers attempt to exploit vulnerabilities in real-time, providing both preventive and detective controls. For teams running Kubernetes workloads, the eBPF approach provides deep visibility without requiring agent installation in every container.
Limitations
Runtime analysis only works for code that's already deployed. You don't get security feedback during development or in pull requests, which means vulnerabilities might reach production before you know about them. The shift-left philosophy that most security teams embrace—catching issues before they're deployed—doesn't apply here.
Runtime monitoring also requires production instrumentation, which some security teams are comfortable with and others aren't. There's a philosophical question about whether you want your security tooling observing production traffic and application behavior, even if the performance overhead is minimal.
Who should consider it
- Teams with mature CI/CD pipelines who want to complement shift-left scanning with runtime validation
- Organizations struggling to prioritize massive vulnerability backlogs and needing production context to focus remediation efforts
- Security programs that have the basics covered and want to add runtime threat detection
6. Cloud security alternative: Wiz Code
For organizations where cloud infrastructure security is the priority and application security is a secondary concern, Wiz provides comprehensive cloud-native application protection (CNAPP) with some AppSec capabilities.
What it includes
Wiz has been expanding into AppSec with code scanning capabilities with the introduction of Wiz Code, but this remains secondary to its core cloud infrastructure focus. The platform offers SCA, IaC scanning, and secrets detection, though it relies on integrating third-party scanners like Checkmarx for deeper SAST analysis rather than building native capabilities.
Where Wiz shines is connecting application risks to cloud and runtime context. If you're already using Snyk or another AppSec tool, Wiz can ingest those findings and enrich them with cloud context to show which vulnerabilities exist in internet-exposed workloads versus isolated environments. This complementary approach works well for enterprises with the budget for multiple specialized tools.
Limitations
The challenge is that Wiz's AppSec features aren't designed for deep developer workflow integration. The platform is built for security teams monitoring production environments, not developers working in IDEs and pull requests. If your goal is shifting security left and embedding it into development workflows, Wiz isn't optimized for that use case.
Who should consider it
- Cloud-heavy organizations where infrastructure security is the primary concern
- Teams that need comprehensive multi-cloud visibility and risk correlation
- Security programs willing to maintain separate tools for AppSec (development) and cloud security (production), or those looking to complement existing AppSec tools with runtime cloud context
7. Snyk alternative for small teams: Aikido Security
For small teams just starting out, Aikido Security provides a compelling alternative to Snyk by wrapping open source tools (opengrep, syft, trivy) into a unified dashboard with a thoughtful UI.
What it includes
Aikido consolidates multiple open source scanners into one platform. You get SAST, SCA, container scanning, IaC analysis, and secrets detection without managing each tool separately. The dashboard provides a single view into findings, and the UI is genuinely well-designed.
For small teams just starting their security journey, this consolidation matters. You're not maintaining multiple tools, writing custom integrations, or building dashboards. Aikido handles that operational overhead so you can focus on actually fixing vulnerabilities.
Limitations
As organizations grow, Aikido's approach becomes harder to operationalize at scale. What makes it great for small teams works against it in growing organizations. The platform relies on wrapping existing open source tools rather than building native capabilities, which limits how deeply it can optimize for accuracy, performance, or advanced features like sophisticated reachability analysis. It also forces you into feeds to review, and lacks a granular policy engine to automate workflows at scale.
Enterprise needs around fine-grained policies, custom workflows, and deep integrations with complex toolchains start exposing these limitations. Teams that initially adopted Aikido for its simplicity often find they've outgrown it as their security program matures.
Who should consider it
- Small engineering teams (under 25 developers)
- Organizations that prioritize ease of setup over depth of capabilities
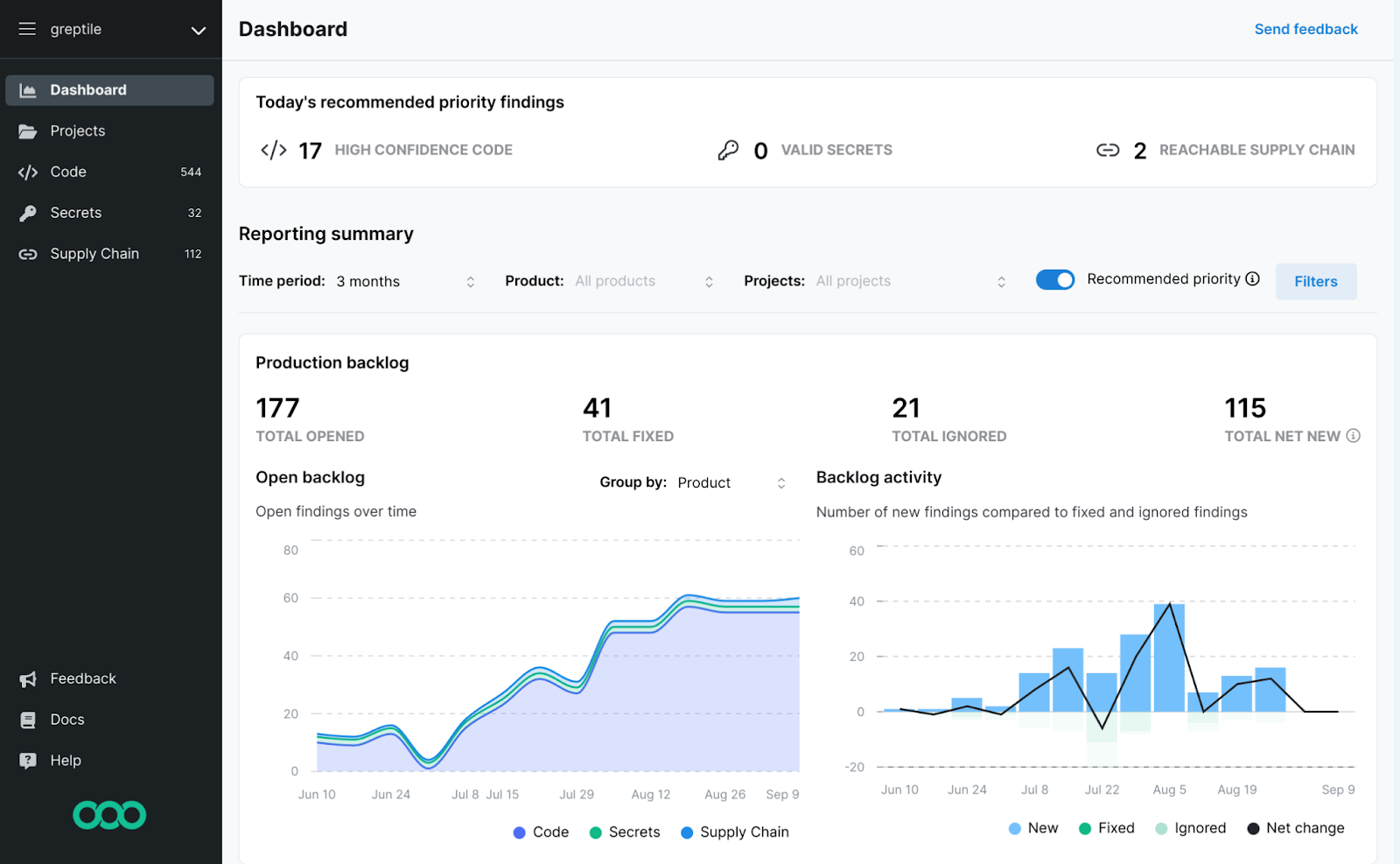
Choosing the right Snyk alternative
Switching security tools is a significant decision. It affects developer workflows, creates migration overhead, and typically requires executive buy-in. So how do you decide which alternative makes sense?
- Start with the problem you're solving. If alert fatigue and developer trust are your primary issues, you need a platform with sophisticated reachability analysis and low false positives. That points toward Endor Labs or similar enterprise platforms. If cost is the constraint and you have security engineering resources, open source tools like Trivy might be sufficient.
- Evaluate your build environment. Teams using Bazel, monorepos, or older languages like C/C++ should verify that alternatives actually support these environments well. Many tools check a box for "Bazel support" without providing the depth needed for accurate results. Only Endor Labs provides full coverage for older languages like C/C++ and modern monorepos built with Bazel.
- Consider AI strategy. If you're building AI-native applications or using AI coding assistants extensively, you need security tools that can keep pace. AI model discovery, AI-BOM generation, and AI security code review aren't nice-to-haves—they're fundamental requirements for securing modern development workflows. Make sure your alternative has these capabilities in production, not on a roadmap.
- Run a proof of value. Most vendors will try to game benchmark repositories, so make sure you scope a PoV against your actual repositories. Demand concrete metrics: How many findings does each tool generate? How many are false positives? What's the noise reduction? How long does it take your team to triage results? Compare these numbers directly against your current Snyk deployment.
- Talk to references. Ask vendors for customers who switched from Snyk and can speak to the migration experience. What was harder than expected? What got easier? How long did it take developers to adjust? These conversations reveal details you won't find in marketing materials.
Snyk alternatives comparison table
Conclusion
The application security tool market has matured significantly in the past few years. You have real choices now—tools designed to solve the specific problems that legacy platforms like Snyk struggle with. The teams succeeding aren't those settling for noise and alert fatigue. They're the ones demanding accuracy, building developer trust, and choosing platforms architected for how modern engineering teams actually work.
Whether you need enterprise-grade reachability analysis, runtime validation, cloud-native security, or cost-effective open source tools, there's a Snyk alternative that fits your requirements. The key is understanding your team's specific pain points and choosing a solution that addresses them rather than creating new friction.
Curious how Endor Labs delivers application security that seamlessly integrates into your development workflows? Schedule a demo to see what accurate, actionable security looks like in practice.
Frequently asked questions about Snyk alternatives
What is the best alternative to Snyk?
The best Snyk alternative depends on your organization's size, technical stack, and primary pain points. For teams focused on reducing false positives and improving developer experience, Endor Labs provides the most comprehensive solution with AI-native analysis and full-stack reachability across code, open source dependencies, and container images.
Why do companies switch from Snyk?
Companies typically switch from Snyk due to alert fatigue from high false positive rates, shallow reachability analysis that doesn't extend to transitive dependencies, inconsistent results between CLI and SCM integrations, and gaps between AI marketing promises and actual product capabilities. Organizations report reducing security tickets by up to 95% after switching to alternatives with better reachability analysis.
Is Endor Labs better than Snyk?
Endor Labs is specifically designed to address Snyk's core limitations. It provides function-level reachability analysis across the entire application graph (including transitive dependencies), AI-native SAST with 95% false positive reduction, and production-ready AI governance capabilities. Companies like Atlassian, Cursor, Dropbox, and OpenAI choose Endor Labs to reduce noise and rebuild developer trust.
What are the limitations of Snyk?
Snyk's main limitations include: high false positive rates without adequate exploitability context, reachability analysis that doesn't extend to transitive dependencies, inconsistent scanning results between different integration methods, limited support for complex build systems like Bazel, and AI capabilities that remain largely on the roadmap rather than in production.
Are there free alternatives to Snyk?
Yes, several free and open source alternatives exist. Trivy, Syft, and Opengrep provide vulnerability scanning, SBOM generation, and SAST capabilities at no cost. GitHub Advanced Security offers a freemium tier for public repositories. However, these options require significant engineering investment to operationalize and don't include enterprise features like centralized policy management or automatic triage.



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:









