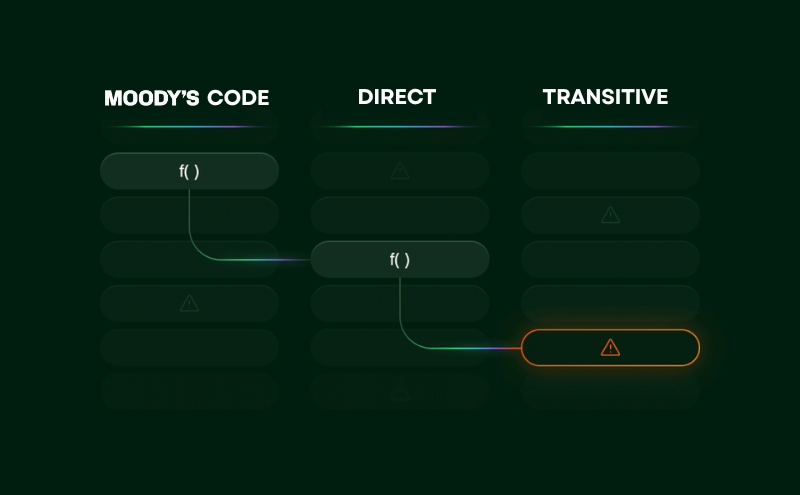
SCA, but with reachability analysis that cuts 92% of noise at

Sensitive financial and risk-related data needs more than superficial scanning. Noisy findings and confusing user interfaces make managing vulnerabilities harder than it has to be. Endor Labs prioritizes function-reachable vulnerabilities, and provides specific evidence needed to fix what (actually) matters.

How it works
Identify all dependencies
Go beyond checkbox SCA to discover all direct and transitive dependencies, including AI models and services.
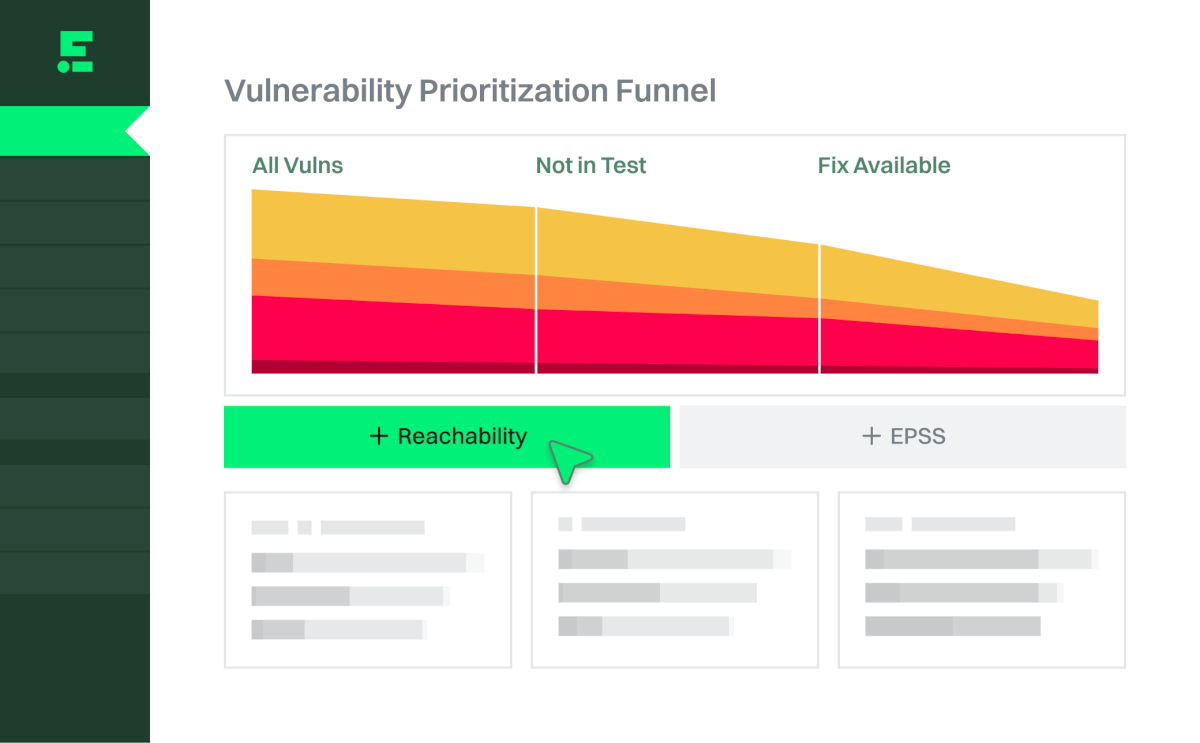
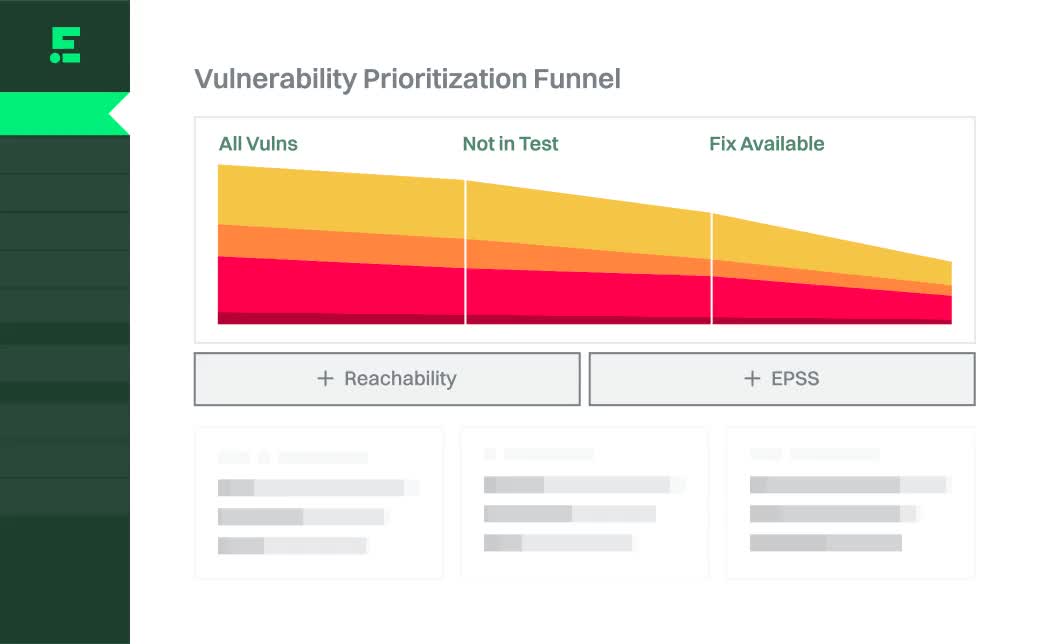
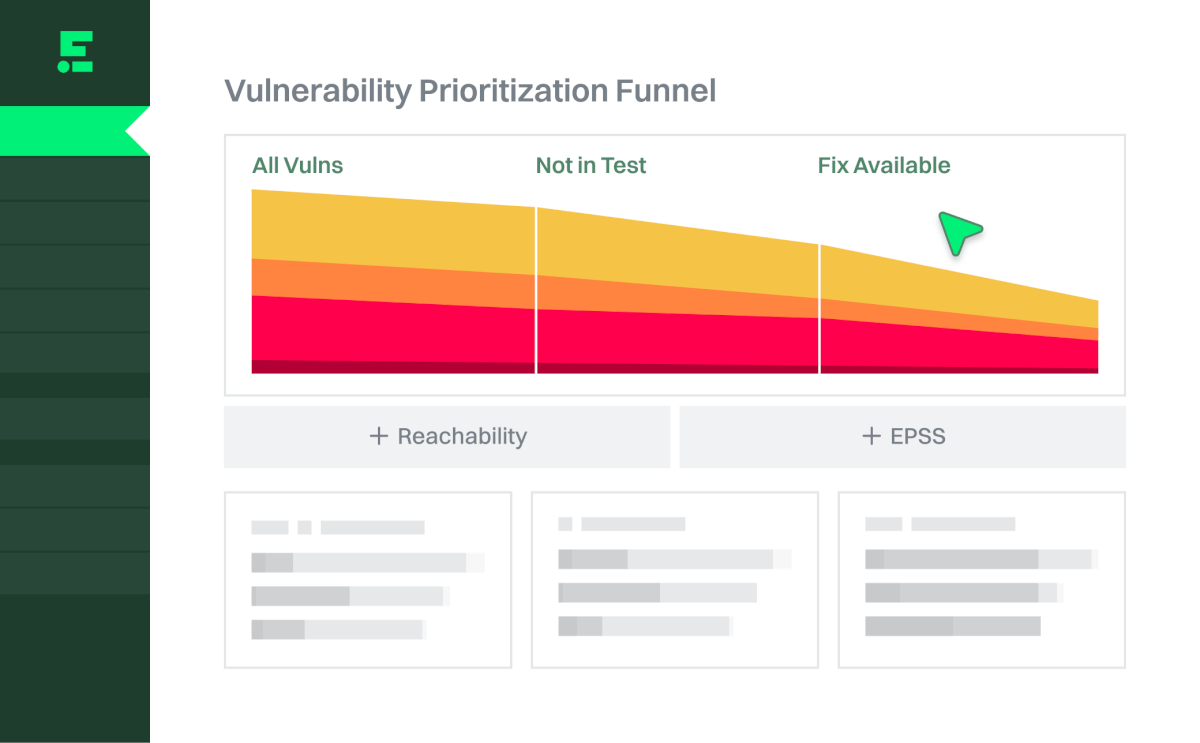
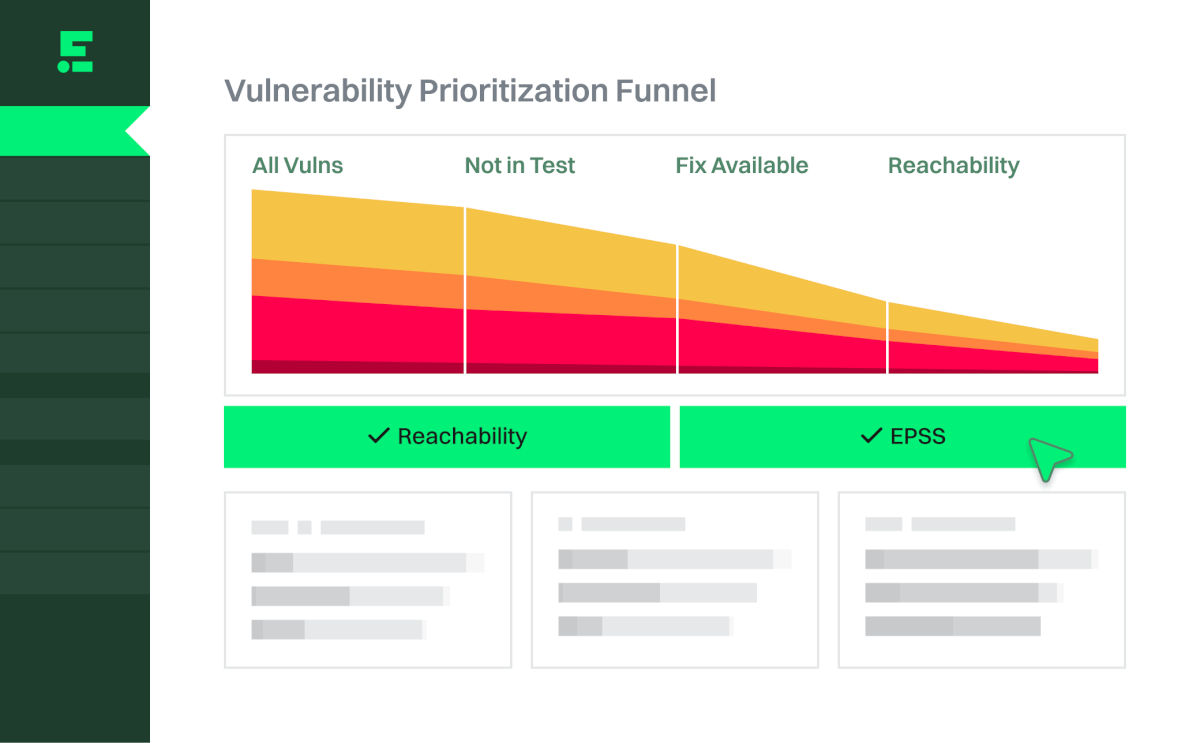
Prioritize by danger
Combine reachability and EPSS to determine which vulnerabilities are the most critical, so you can remediate those first.
Fix faster
Identify upgrades that can be performed without risk of breaking changes and help engineering plan for the hard ones.
Securing code written by humans and AI at:


































































We have been pleasantly surprised about the lack of friction when trying new features outside, like container scanning, that are outside the traditional SCA scope. It took us just five minutes to set up a CircleCI job and give it a container from our registry, and we were immediately seeing results."