AppSec for the
Software Development Revolution
From 40 year-old C++ to Bazel Monorepos, Endor Labs has you covered.








































In just the first week we saw an 80% reduction in risks we had to remediate, all due to reachability analysis — and we continue to see that number climb.





Analyze every line of code, every dependency, on every layer.
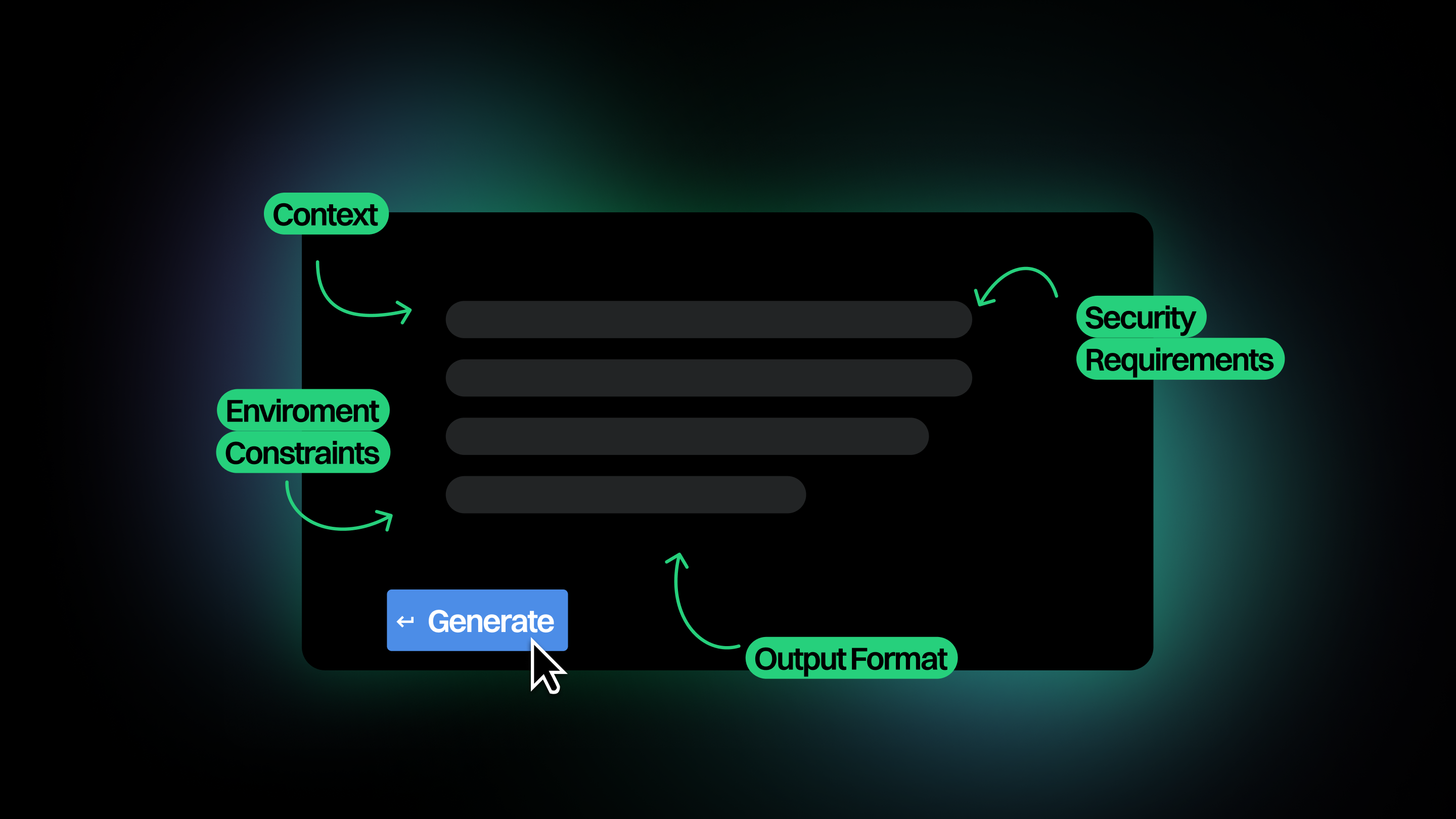
Code Scanning Built To Reduce Noise
Endor Labs graphs how your application works across your code, open source dependencies, containers, and CI/CD workflows. That means your SCA, SAST, Secrets, and Container findings are clean, actionable, and in a single place.
.gif)

Remediation That Actually Fixes Things
Endor Labs uses program analysis to identify which vulnerabilities actually pose risk to your application, then offers multiple paths to fix them: see what would break in an upgrade with Upgrade Impact Analysis, or apply just the security fix without upgrading using Endor Patches.
AI in Dev, AI in AppSec — We’ve Got It Covered
Endor Labs identifies risks in AI models and AI-generated code, tracks AI model provenance, and enforces proper governance. We also use AI to improve security team productivity - automatically analyzing thousands of pull requests to identify the handful with significant security implications, summarizing complex code changes in plain language, and providing contextual insights about risks.
The Right Tools & APIs to Shift Left
Endor Labs' API-first policy engine replaces noisy, generic security rules with precise policies tailored to your risks and workflows. By surfacing only meaningful, reachable issues and automating targeted actions, it drastically cuts unnecessary build breaks and security tickets—letting developers focus on building, not fixing.


Don't take our word for it
Andrey Kolesnikov
CEO, MileIQ

VMware
Director, Corporate Compliance and GRC Transformation
Azeem Nizam
CISO, ABC Fitness

Clark Smith
CISO & Managing Director at Citi
David Tsao
CISO, Instacart

Arif Janmohamed
Partner at Lightspeed Venture Partners
DevSecOps Engineer
G2 Review

Matt Carbonara
Head of Enterprise Tech Investing at Citi Ventures
VMware Cloud Services
Global Head of InfoSec & GRC Strategy

Bipul Sinha
CEO, Rubrik
VMware
Director, Corporate Compliance and GRC Transformation

Aparna Bawa
COO, Zoom
Rachit Lohani
CTO, Paylocity

Greg Pettengill
Principal Security Engineer at Five9
Andrey Kolesnikov
CEO, MileIQ

VMware
Director, Corporate Compliance and GRC Transformation
David Tsao
CISO, Instacart

Arif Janmohamed
Partner at Lightspeed Venture Partners
VMware Cloud Services
Global Head of InfoSec & GRC Strategy

Bipul Sinha
CEO, Rubrik
VMware
Director, Corporate Compliance and GRC Transformation

Aparna Bawa
COO, Zoom
Rachit Lohani
CTO, Paylocity

Greg Pettengill
Principal Security Engineer at Five9
Andrey Kolesnikov
CEO, MileIQ

VMware
Director, Corporate Compliance and GRC Transformation
Azeem Nizam
CISO, ABC Fitness

Clark Smith
CISO & Managing Director at Citi
David Tsao
CISO, Instacart

Arif Janmohamed
Partner at Lightspeed Venture Partners
DevSecOps Engineer
G2 Review

Matt Carbonara
Head of Enterprise Tech Investing at Citi Ventures
VMware Cloud Services
Global Head of InfoSec & GRC Strategy

Bipul Sinha
CEO, Rubrik
VMware
Director, Corporate Compliance and GRC Transformation

Aparna Bawa
COO, Zoom
Rachit Lohani
CTO, Paylocity

Greg Pettengill
Principal Security Engineer at Five9
Andrey Kolesnikov
CEO, MileIQ

VMware
Director, Corporate Compliance and GRC Transformation
David Tsao
CISO, Instacart

Arif Janmohamed
Partner at Lightspeed Venture Partners
VMware Cloud Services
Global Head of InfoSec & GRC Strategy

Bipul Sinha
CEO, Rubrik
VMware
Director, Corporate Compliance and GRC Transformation

Aparna Bawa
COO, Zoom
Rachit Lohani
CTO, Paylocity

Greg Pettengill
Principal Security Engineer at Five9

Implementing software supply chain security
Uplevel app security skills and connect with like-minded people









.webp)