In today’s fast-paced development environments, the biggest security risks often aren’t critical CVEs, they’re misconfigurations, overly broad permissions, and missing controls quietly introduced through everyday code changes.
As an application security engineer, identifying these risks buried in pull requests (PRs) is time-consuming and error-prone. That’s why we built an AI Security Code Review at Endor Labs. It uses multi-agent analysis to detect changes to your application security posture automatically, including Infrastructure as Code (IaC) misconfigurations in tools like Terraform.
Example: Detecting Overly Permissive IAM Policies in Terraform
Let’s say a developer pushed a PR with updates to a Terraform manifest file:
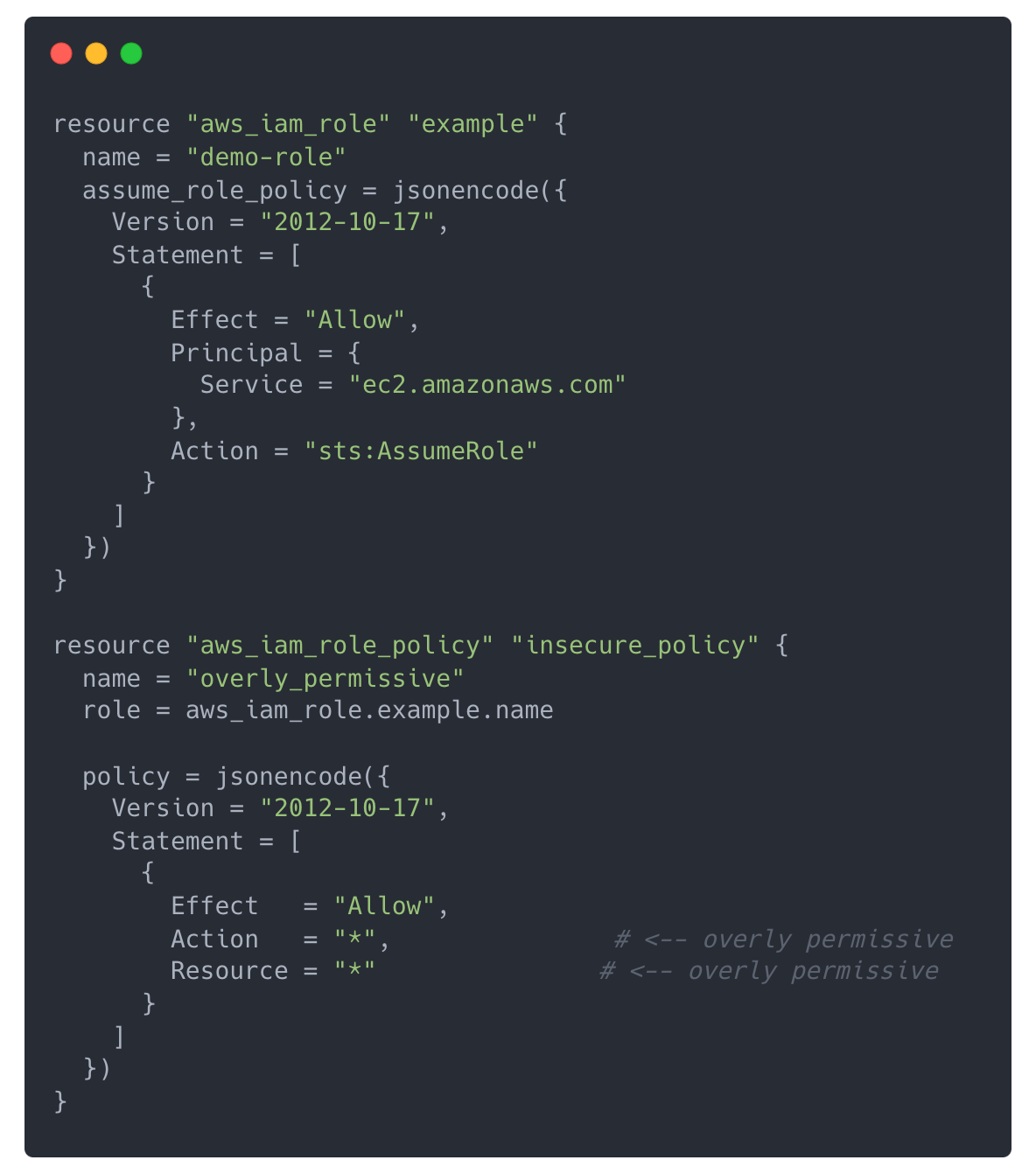
What's the risk?
This policy grants full access to all AWS actions and all resources, violating the principle of least privilege. If deployed, this IAM role could be abused to escalate privileges, exfiltrate data, or compromise other services.
How AI Security Code Review Flags the Risk
Endor Labs uses multiple AI agents to review the PR, categorize the changes, and evaluate them for security impact. When this PR is submitted, Endor Labs’ agents analyze the Terraform diff and post a comment directly in the PR:
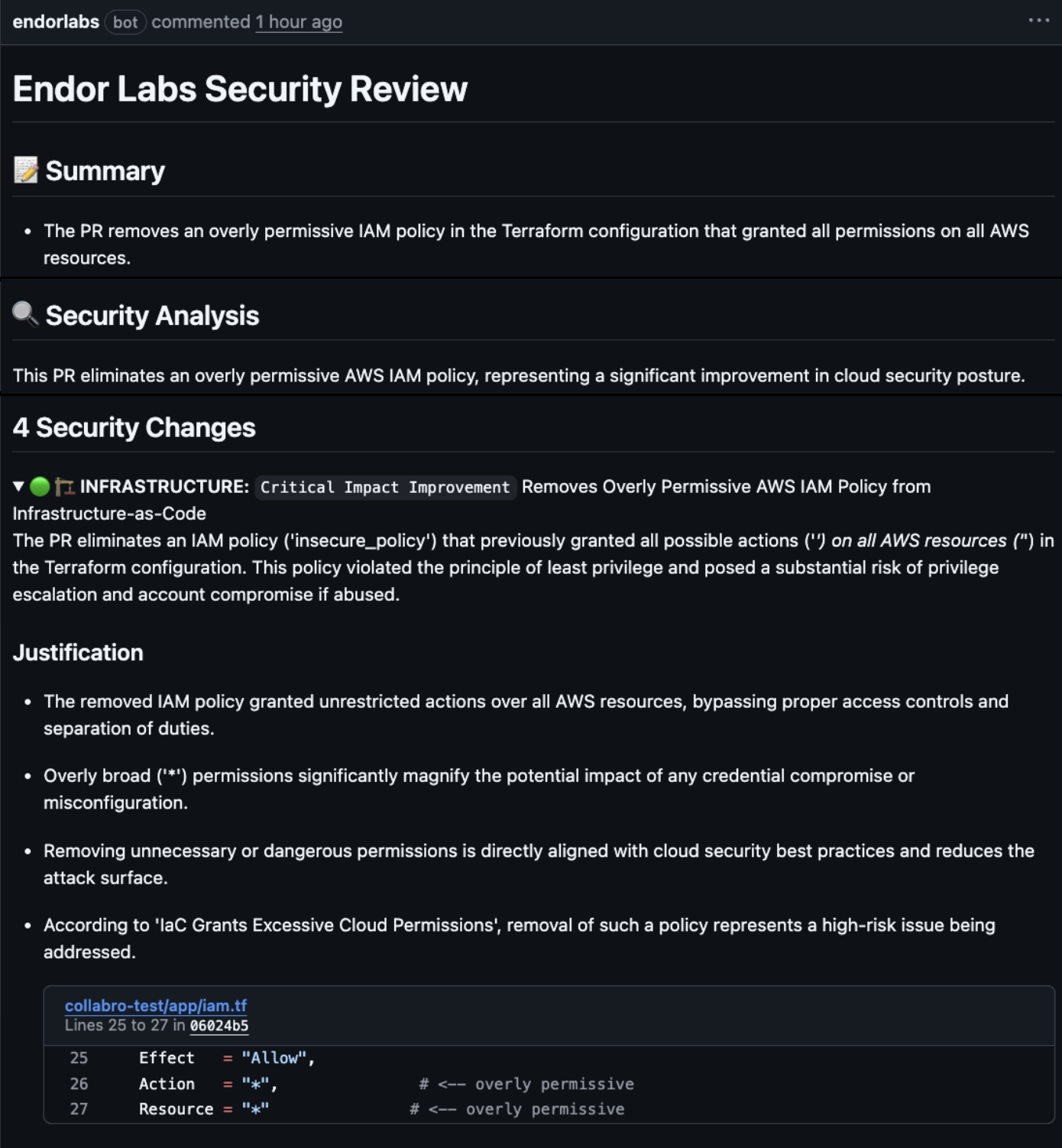
In the Endor Labs UI, every merged PR includes a security posture summary showing what changed and why.
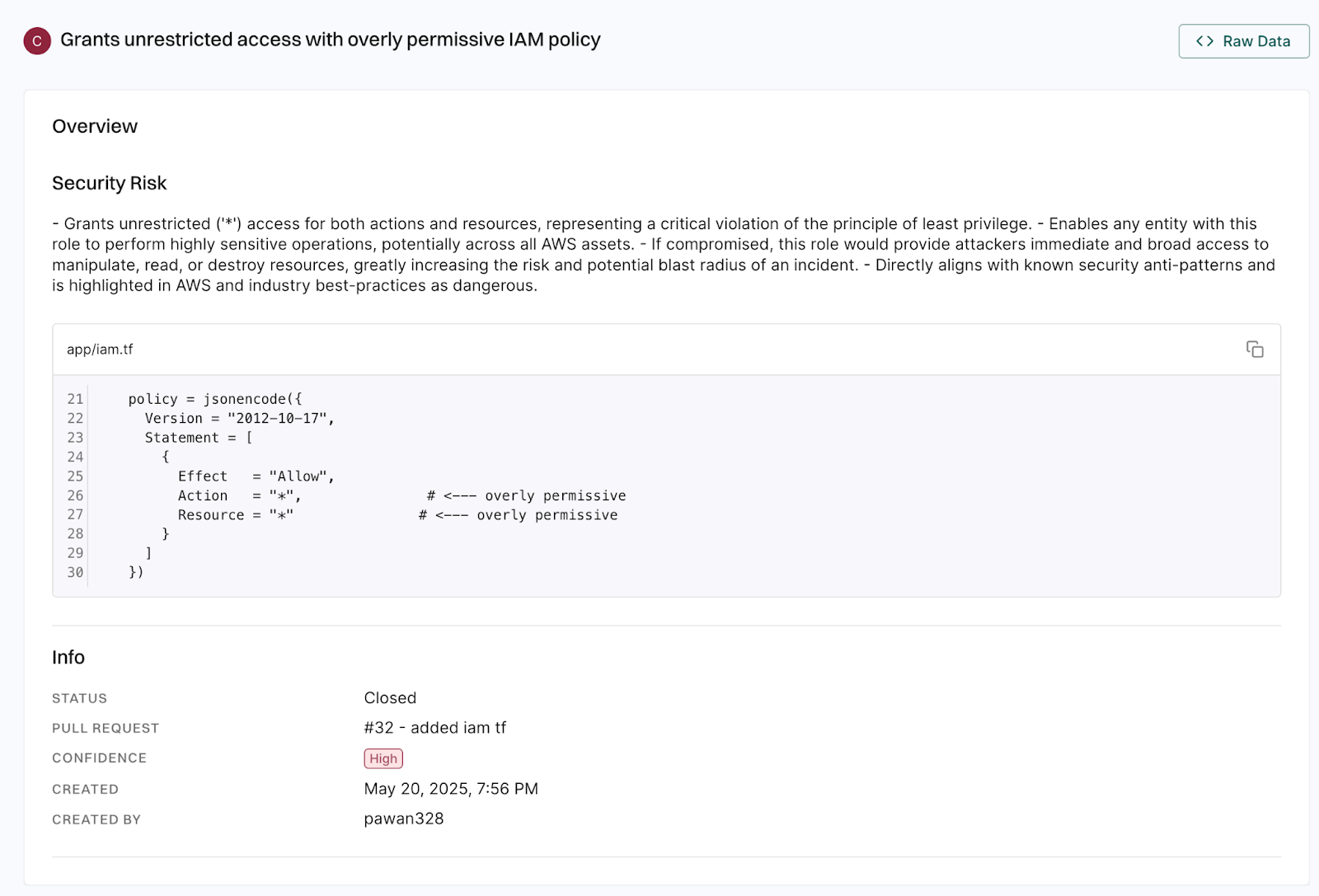
Why is this important?
- IaC is code. Just like app code, infrastructure definitions can introduce critical security flaws.
- Design flaws slip through. SAST and SCA won’t catch over-permissive roles or unsafe defaults in your cloud configurations.
- PRs are the last line of defense. If you catch it here, you prevent drift, misconfigurations, and privilege escalations from ever landing in prod.
Review every PR for security posture changes
Endor Lab’s ability to detect insecure IaC configs in the PR gives your team the confidence that:
- Insecure IAM policies don’t go unchecked
- Least privilege enforcement is visible and reviewable
- Threat modeling assumptions remain aligned with what’s actually deployed
AI Security Code Review turns PRs into proactive security checkpoints. Instead of relying on infrequent architecture reviews or runtime scanning alone, you now have a much more inline, design-aware analysis embedded into your developer workflow.
With multi-agent, context-aware reviews, AppSec moves from chasing issues to preventing them at the source. Read our whitepaper to learn more about our multi-agent approach and other issues you can detect with AI Security Code Review from Endor Labs.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:










