Stop fixing false positives for FedRAMP
Satisfy your 3PAO and meet SLAs without the hassle of remediating things you know aren’t real risks.
4.9 (G2 Reviews)
Stop fixing false positives for FedRAMP
Satisfy your 3PAO and meet SLAs without the hassle of remediating things you know aren’t real risks.


Loved by security teams, painless for developers at:


































































How it works
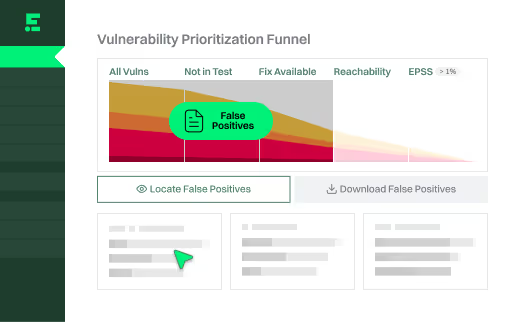
1
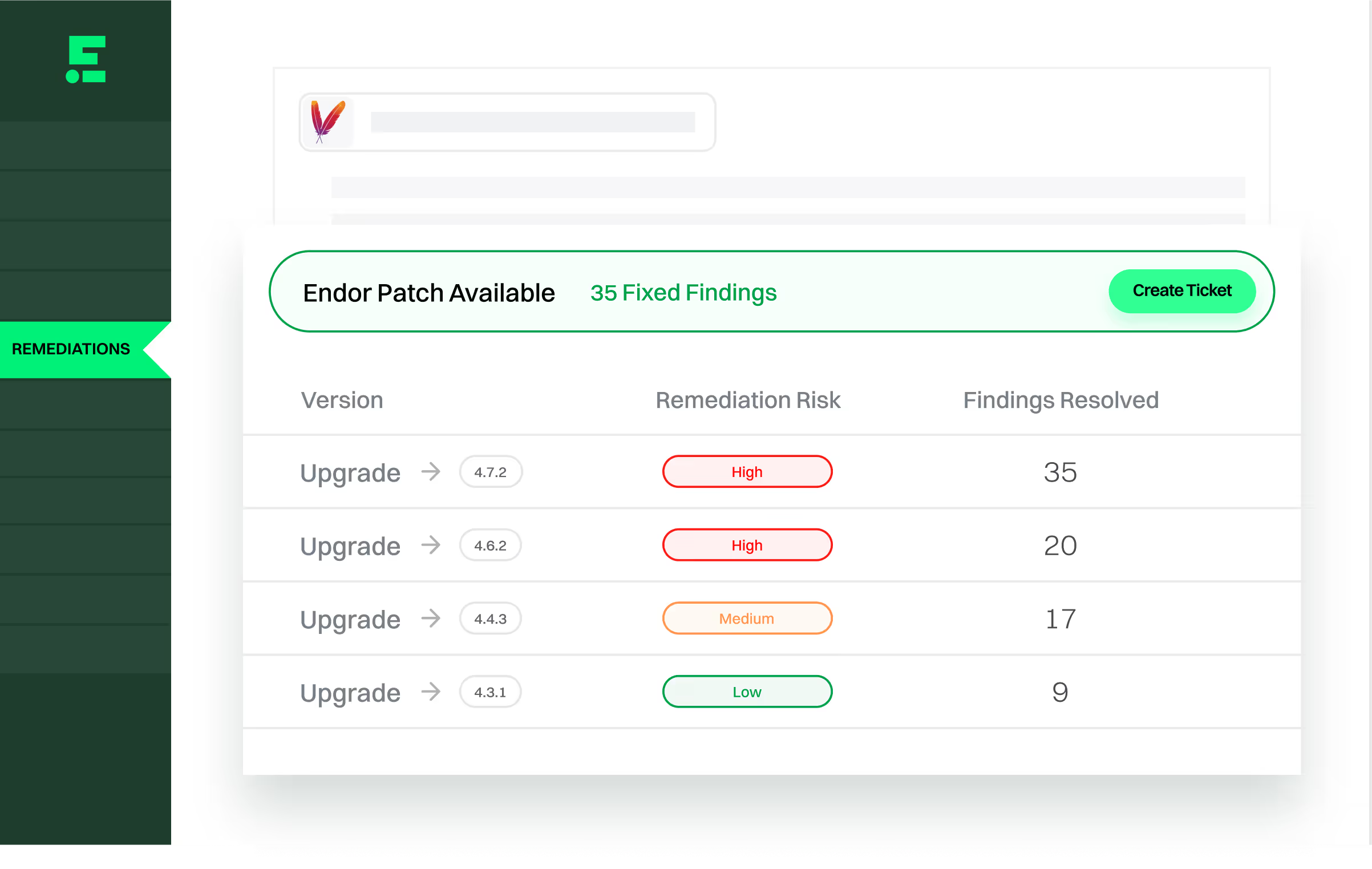
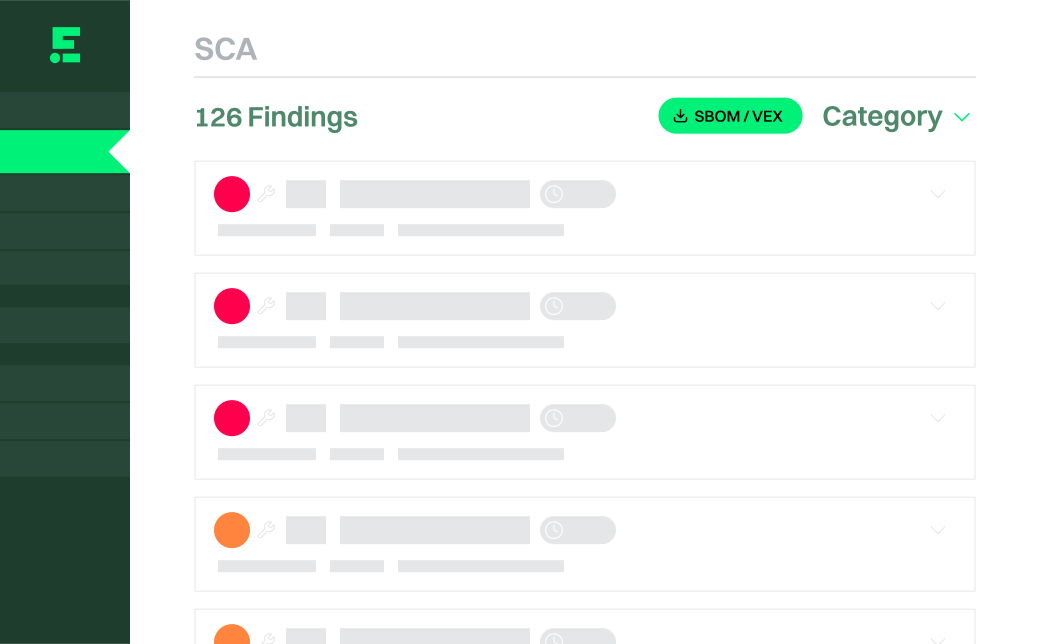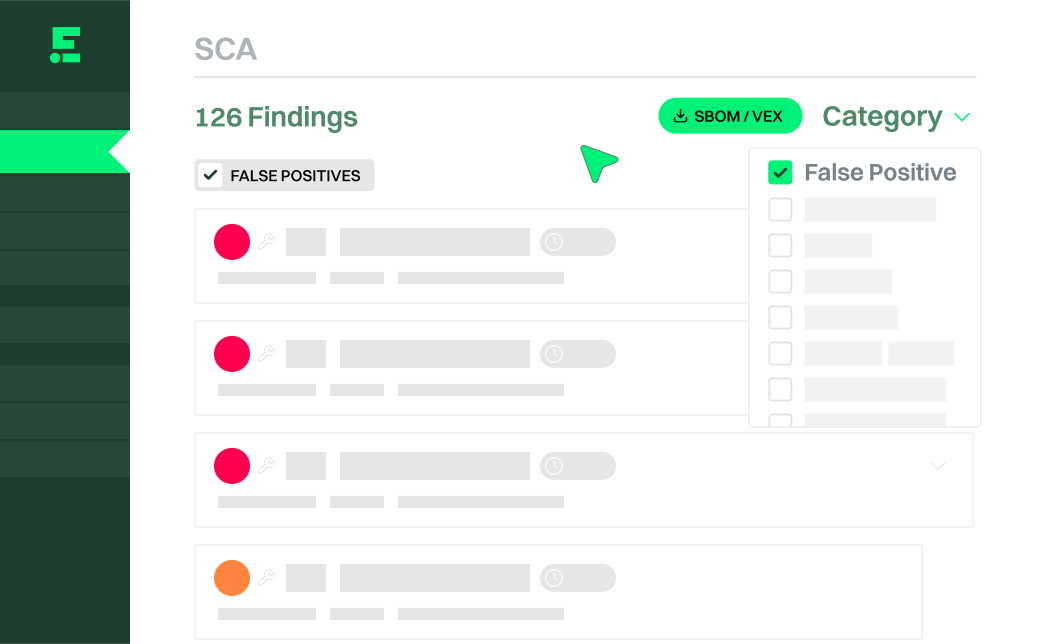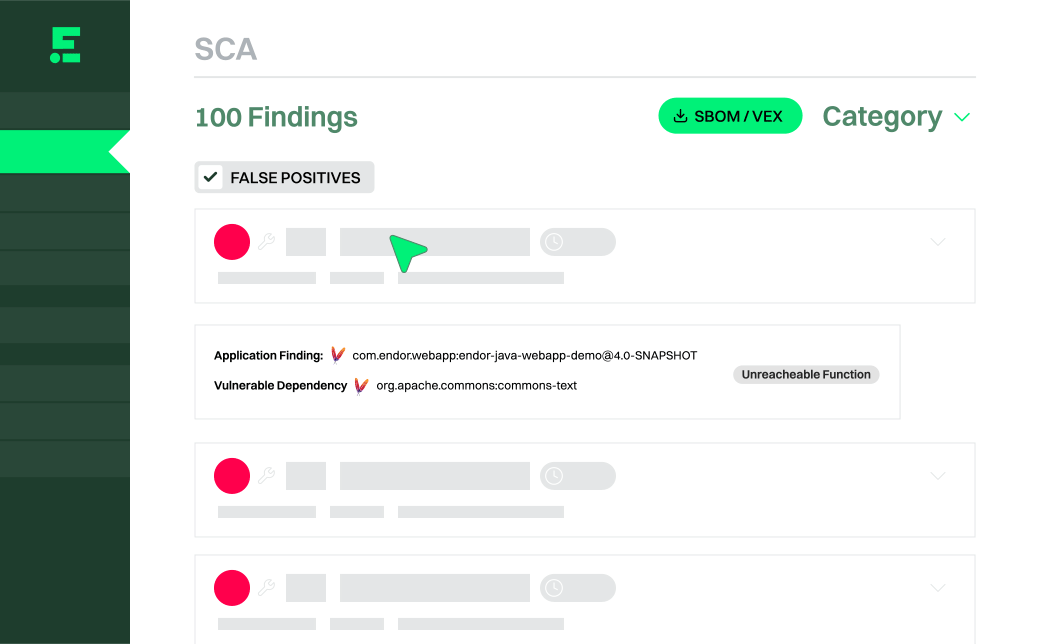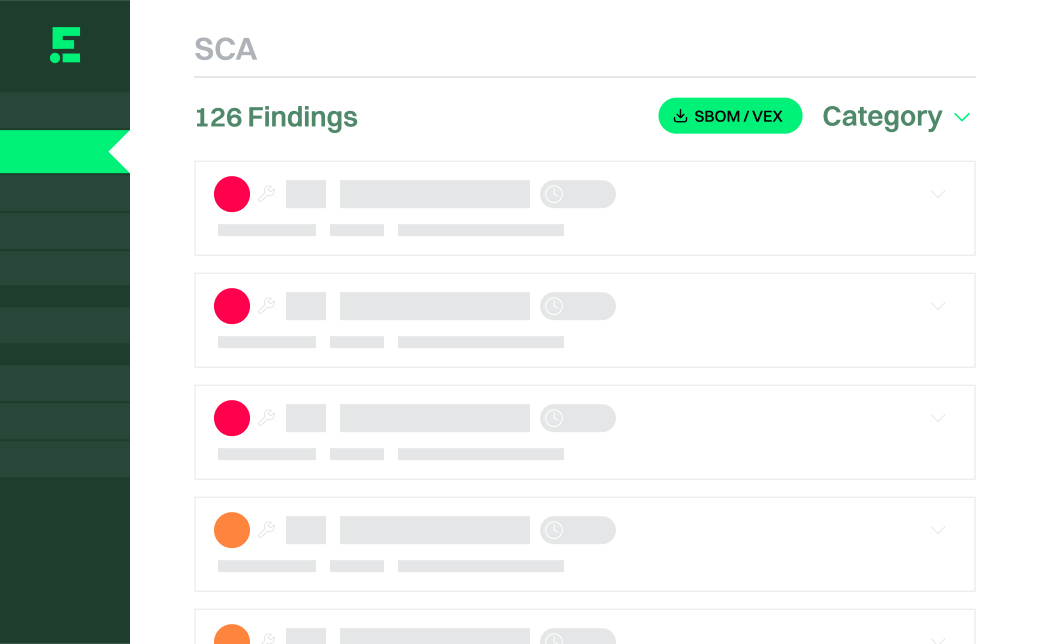
3PAOs accept Endor Labs’ reachability analysis as evidence false positives
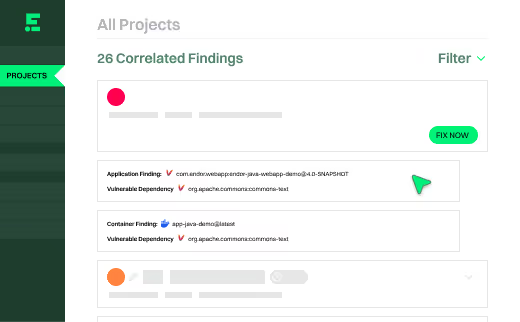
2
Reduce double filings by correlating SCA and container scans
Without the tedium and minutia of tracking down individual items that might not matter, we can focus on the remaining vulnerabilities that would impact customers and our FedRAMP compliance."
Without the tedium and minutia of tracking down individual items that might not matter, we can focus on the remaining vulnerabilities that would impact customers and our FedRAMP compliance."